- Posted by :Admin
- Date :22 Apr, 2021
- Category : Platform
Big month of updates
April was a big month for ATTACKIFY in regards to updates on the platform, this includes a major effort to update front-end and backend components to version 1.3.0 and then we had a number of new modules come in over the last few months. Some of the new & updated modules include:
- Malicious Office Macro Execution
<b><span style="color:#376889;">ATTACK</span><span style="color:#616163;">IFY</span></b> endpoint agents can safely simulate end-users executing "malicious" macro enabled Microsoft Word Documents on Windows.
This module allows security engineers to continuously test and refine security controls around Microsoft Office security. Successful
simulations will execute calculator.exe on Microsoft Windows. Also this module will be improved and extended to support Microsoft Office
on MacOS endpoints.
- .Net createdump.exe LSASS Memory Dump
Attackers are always finding new methods of extracting credentails from LSASS by dumping memory of the process. <b><span style="color:#376889;">ATTACK</span><span style="color:#616163;">IFY</span></b> has a
few simulation modules attacking this area and we have recently included a new method discovered via @bopin2020 that leverages .Net 5.x.x
app, createdump.exe, that ships with default .Net 5 installs on Windows.
- RunDLL Execution Bypass Improvements
We have further improved the rundll32.exe execution bypass simulation module and added new techniques seen in the wild, all
simulations will attempt to execute either cmd.exe or calc.exe in a non-malicious manner but still demonstrate the technique effectively.
- SudoEdit Buffer Overflow
Earlier this year CVE-2021-3156 was made public and we have a module to simulate the attack on Linux endpoints.
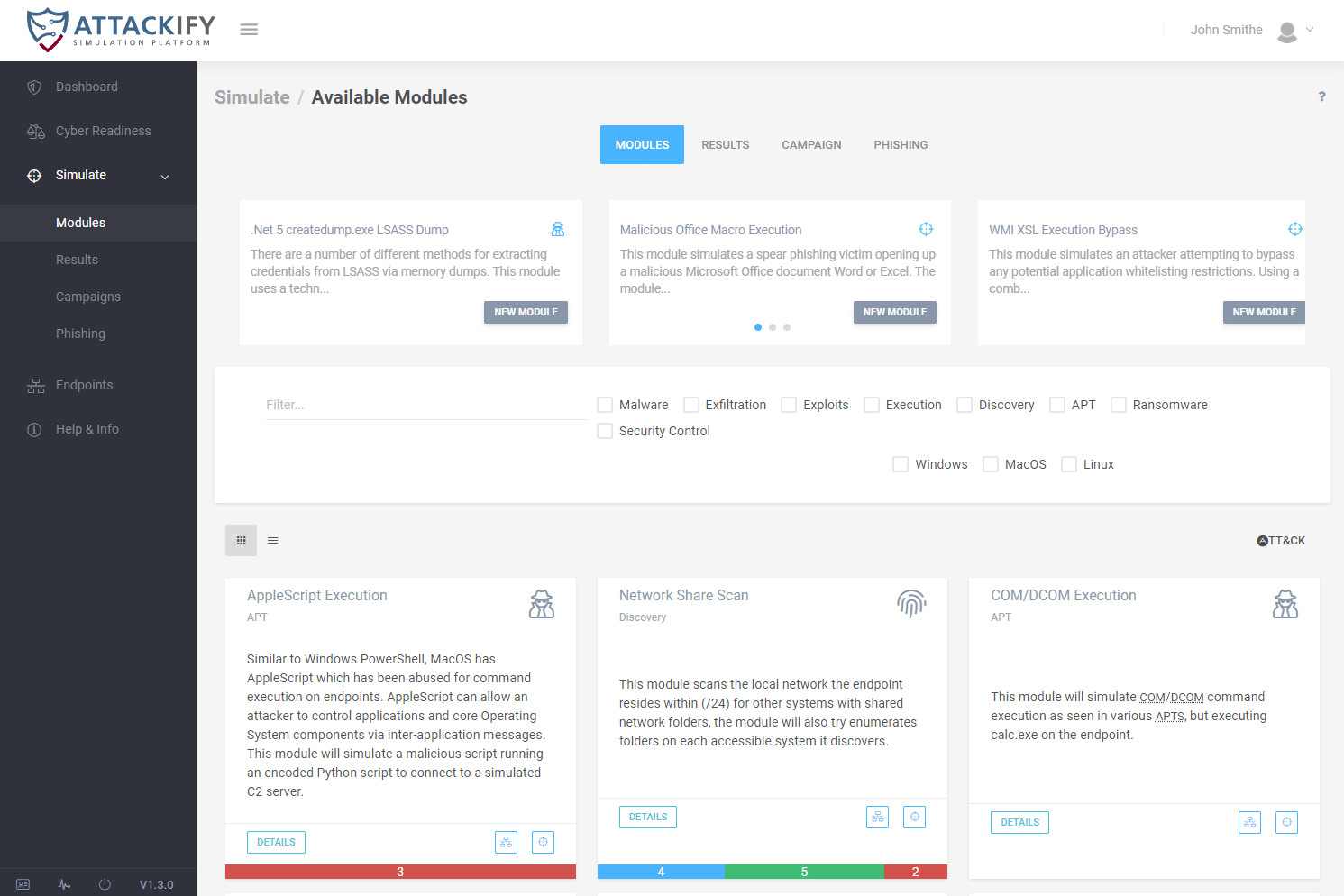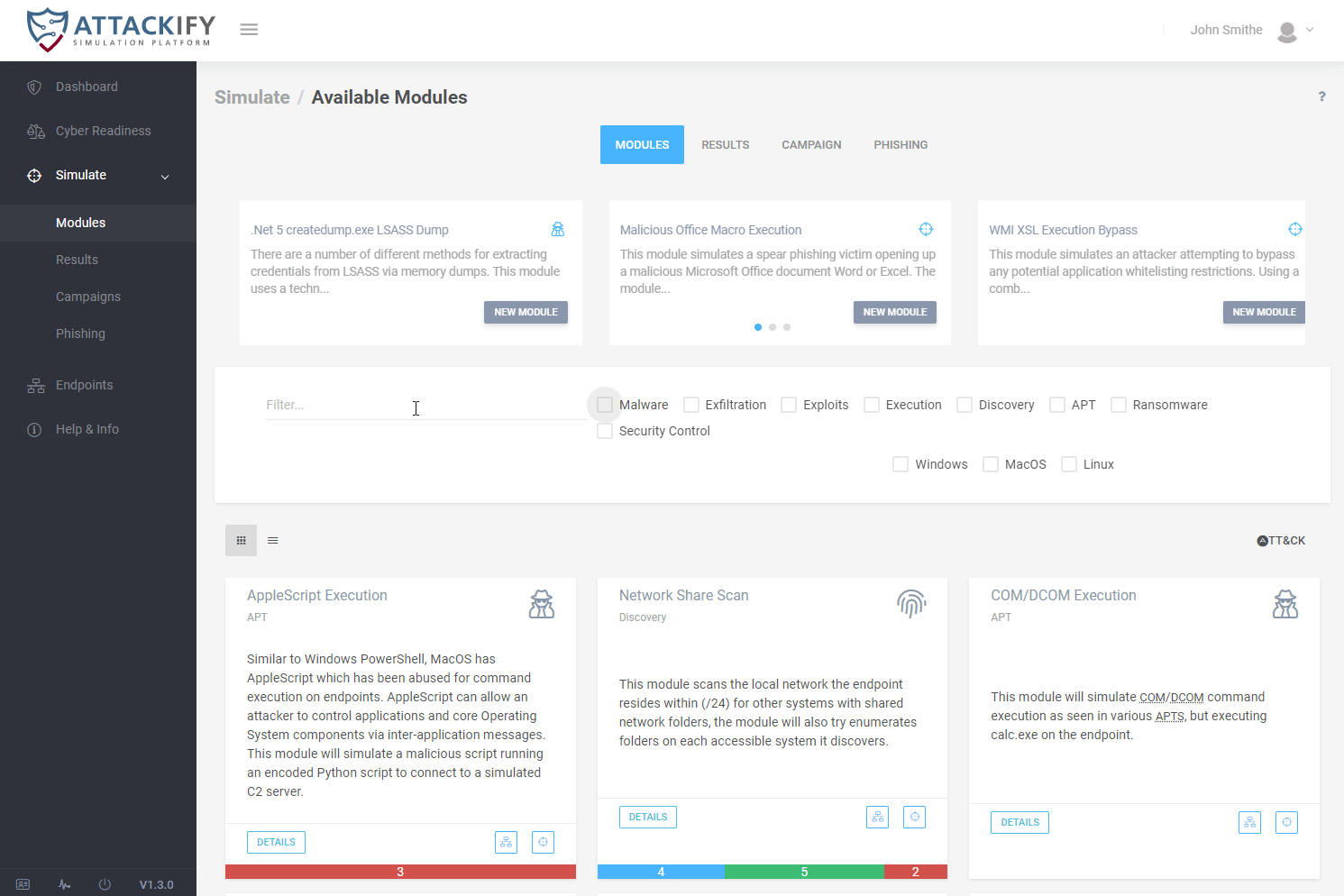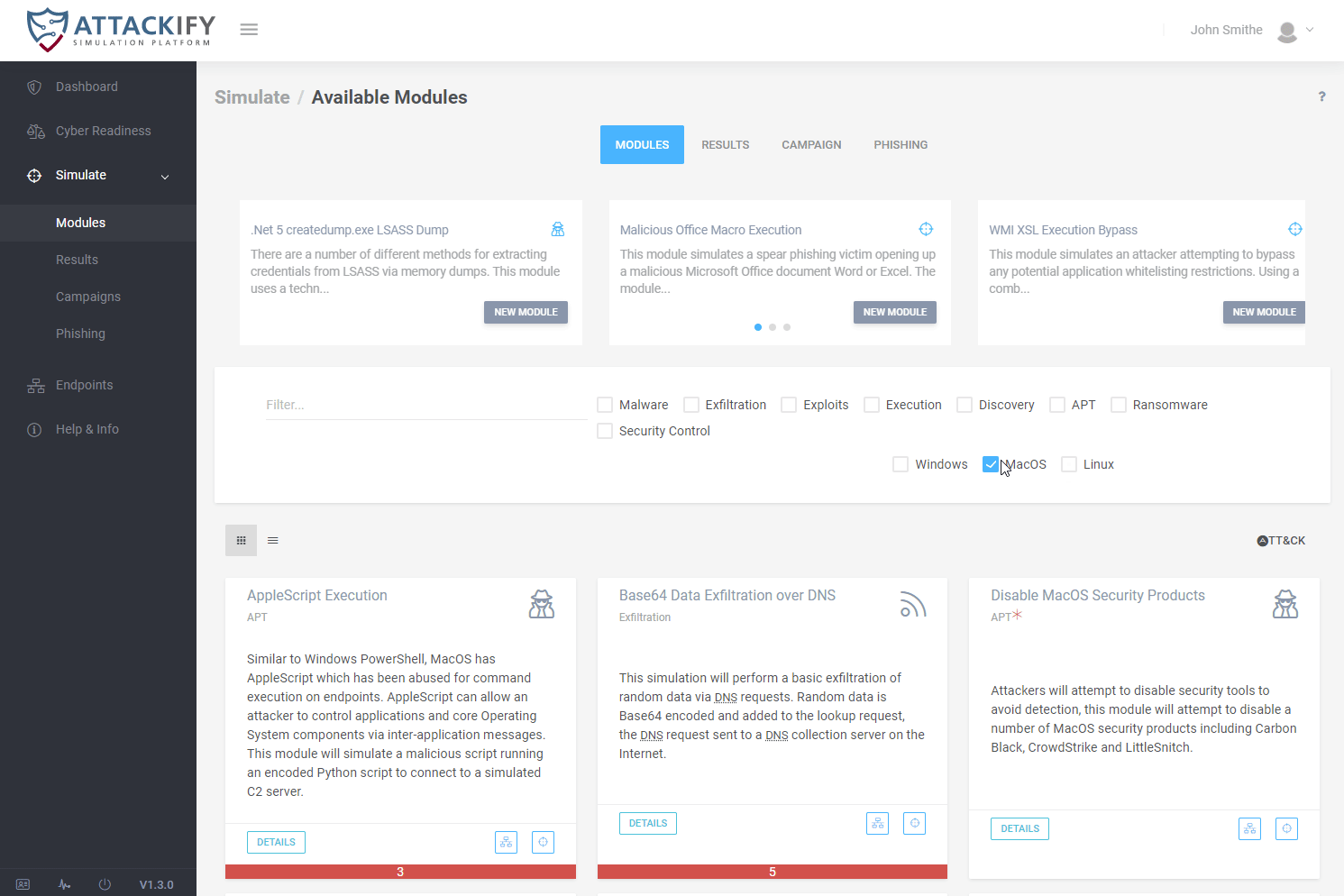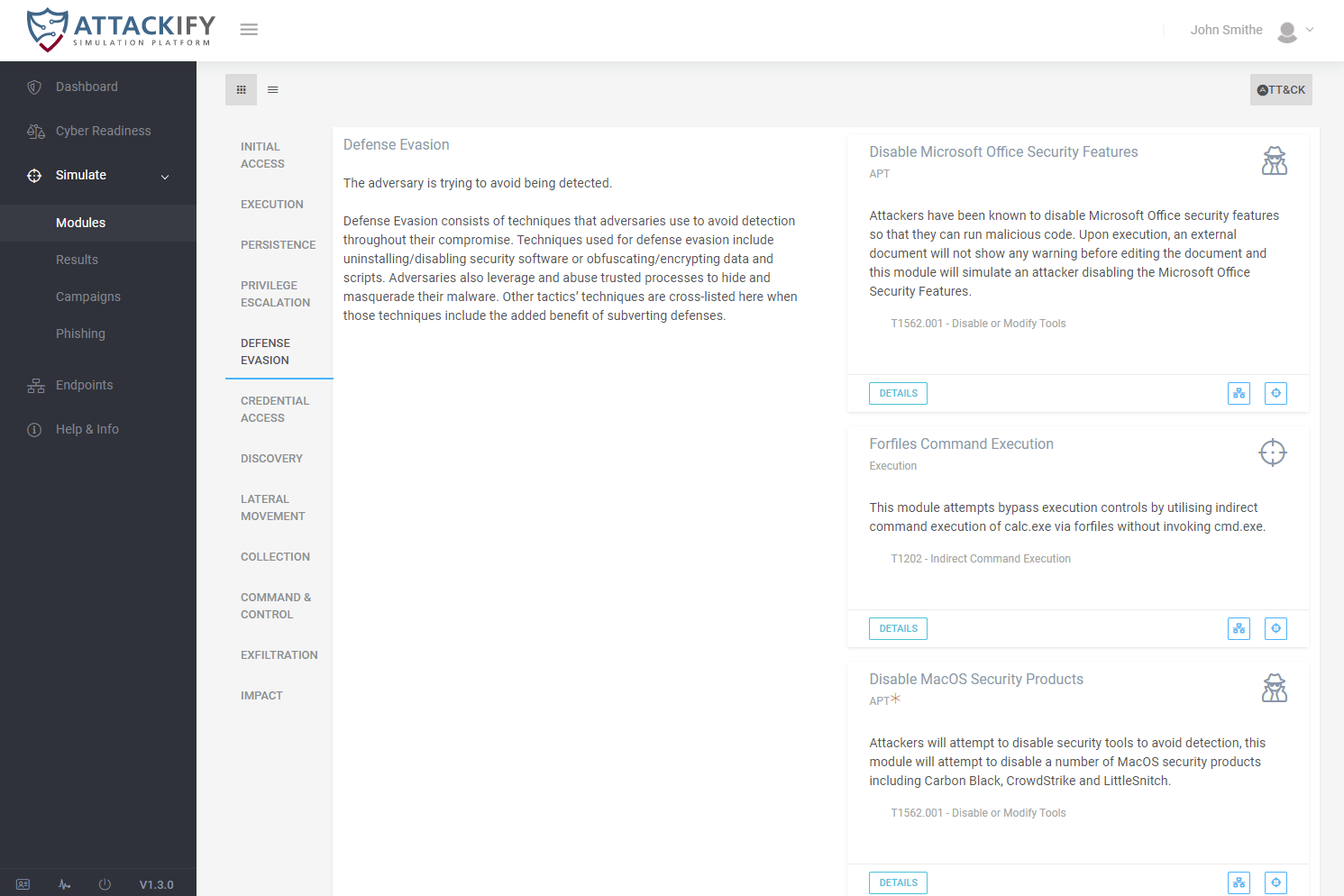
ATTACKIFY Modules
We have been working across various simulation and security control modules for each of the supported endpoint agent platforms we currently have in ATTACKIFY. We can break down some of the stats as follows:
Total Modules by Operating System
- Windows - 81
- MacOS - 28
- Linux - 19
Total Modules by Mitre ATT&CK Framework
- Initial Access - 3
- Execution - 10
- Persistence - 9
- Privilege Escalation - 7
- Defense Evasion - 22
- Credential Access - 4
- Discovery - 14
- Lateral Movement - 6
- Collection - 7
- Command & Control - 15
- Exfiltration - 12
- Impact - 2
Taking our time and ensuring that we add modules that add value is important to ATTACKIFY’s platform, it would be easy to add a few thousand modules that don’t add real value, imagine 5,000 simulations where each one downloads a different known virus into memory…thats not really helpful to security engineers and makes your library look horribly inflated and difficult to use.
We will continue to keep things simple and easy to use!
Is it available yet?
Yes! We have opened up two licensing modules, Starter and Professional…see the pricing section for more details! Also feel free to get in touch with us if you have an interest in ATTACKIFY or curious to get a better understanding of it.