- Posted by :Admin
- Date :11 Jun, 2025
- Category : Platform , Features
Ready to Test Your Defenses Against the Sneakiest Attack Technique?
The cybersecurity world has a new favorite trick, and it’s incredibly hard to catch. Beacon Object Files (BOFs) are like the ninjas of the cyber world—they slip into memory, do their dirty work, and vanish without leaving a trace on disk. Today, we’re thrilled to announce ATTACKIFY’s Cobalt Strike BOF Simulation Modules that let your security team practice defending against these advanced techniques in a safe, controlled environment!
Why BOFs Are Giving Security Teams Nightmares
Think of BOFs as an evolution of cyber attacks. While traditional malware drops files and makes noise, Beacon Object Files are the silent professionals of the threat landscape. Here’s what makes them so challenging:
The Invisible Threat
BOFs execute entirely in memory—no files hit the disk, no obvious process creation, no traditional forensic breadcrumbs. As TrustedSec explains in their developer introduction, BOFs are “compiled C programs written to a convention that allows them to execute within a Beacon process and use internal Beacon APIs.”
Real-World Impact
The numbers don’t lie—Cobalt Strike usage by malicious actors increased by 161% between 2019-2024. APT groups like APT41 and APT29 are actively weaponizing BOF techniques, while ransomware giants like RansomHub (responsible for 531 attacks in 2024) deploy custom BOF payloads for reconnaissance and lateral movement.
Detection Challenges
Traditional security tools struggle because:
- No file signatures = signature-based detection fails
- Memory-only execution = behavioral analysis becomes critical
- Legitimate tool abuse = Cobalt Strike is a legit pen-testing framework
- Minimal network footprint = network monitoring misses the action
ATTACKIFY’s Solution: Realistic BOF Training Without the Risk
Our new simulation modules solve a critical gap—how do you train your blue team against BOF techniques without actually deploying real malware? We’ve created two new modules that bring authentic BOF behavior to your testing environment:
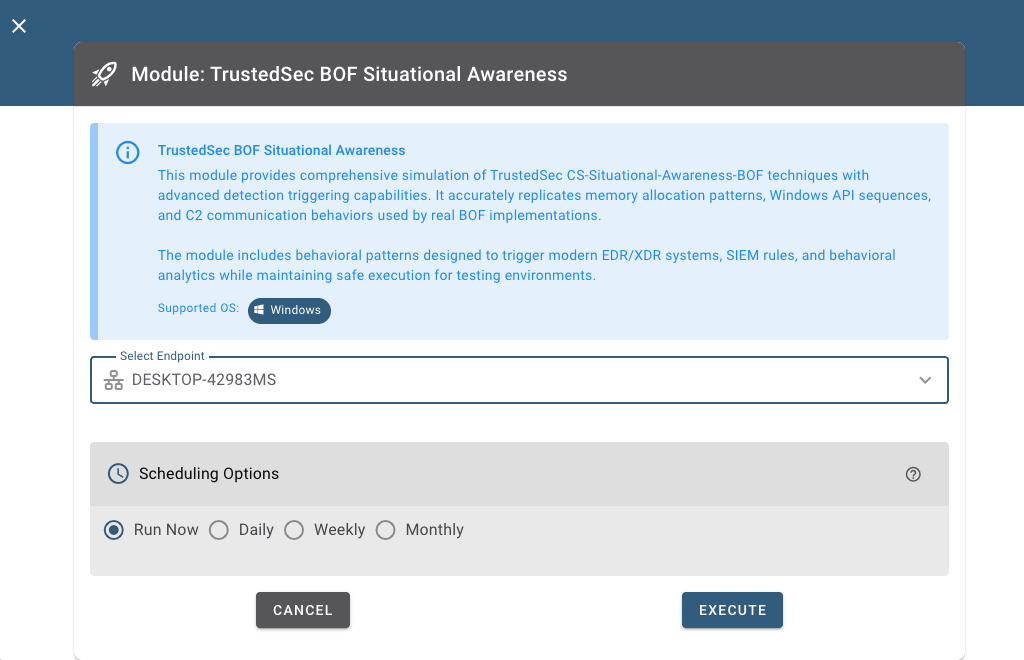
Module 1: Generic Cobalt Strike BOF Simulation
This module simulates the complete BOF execution lifecycle with authentic detection triggers:
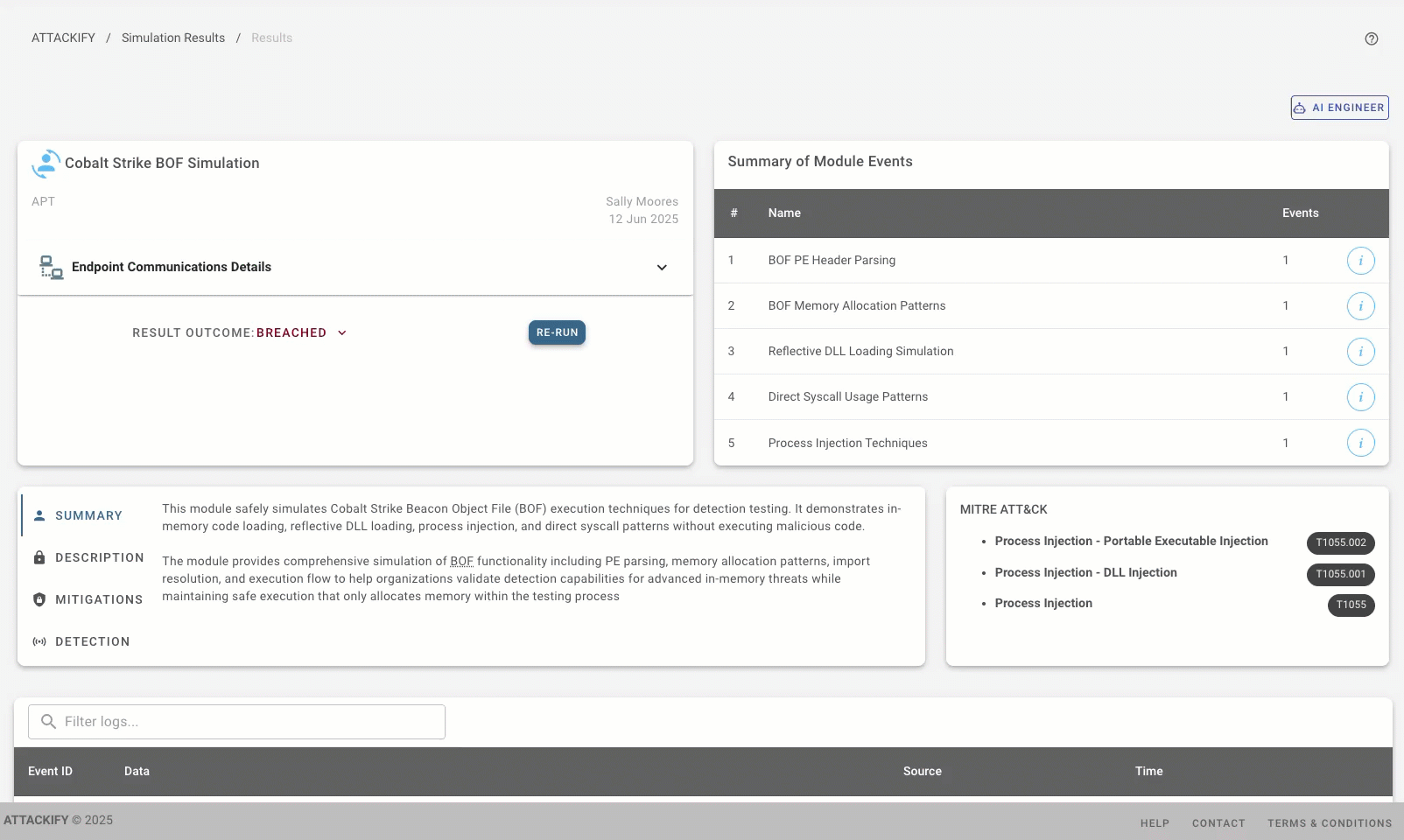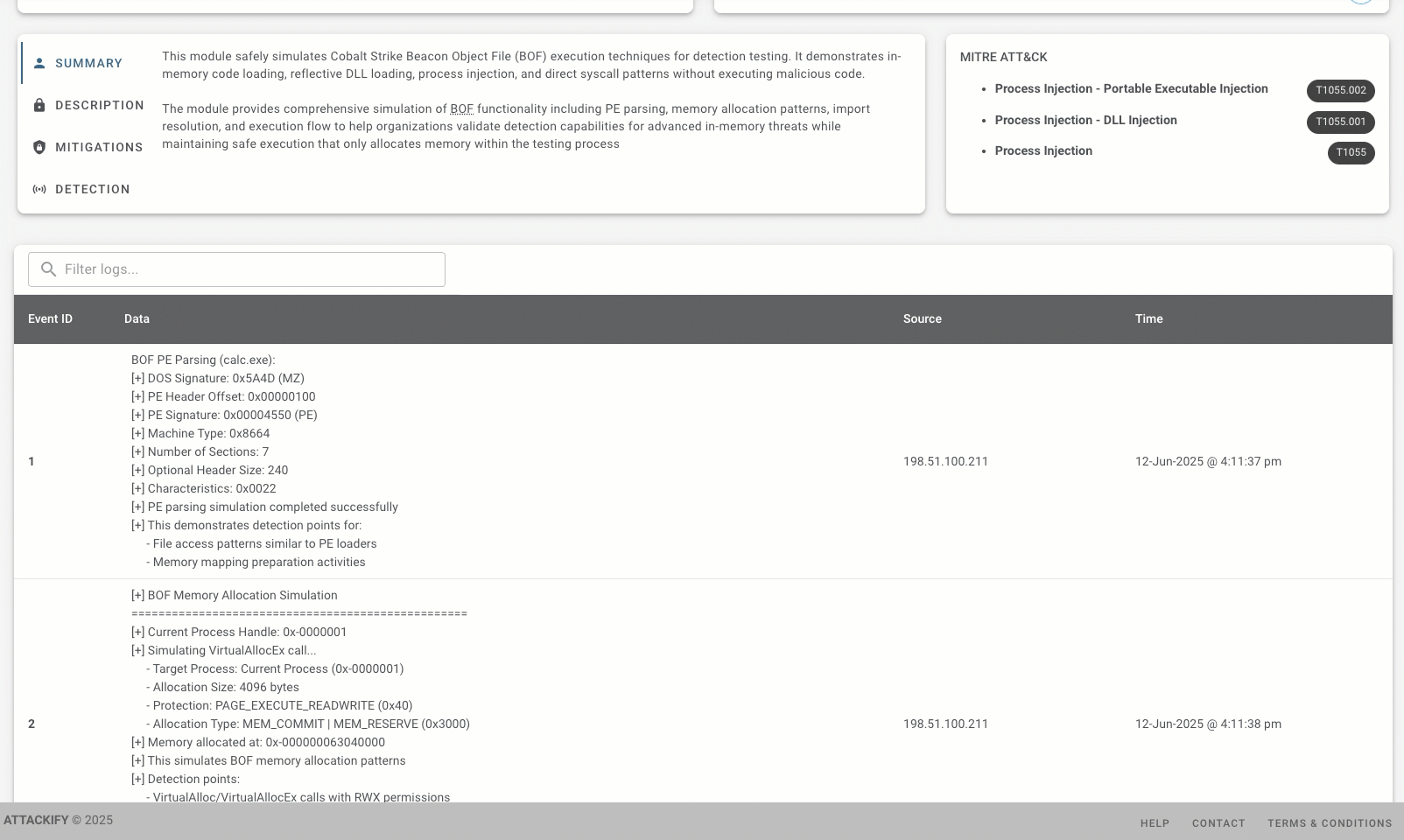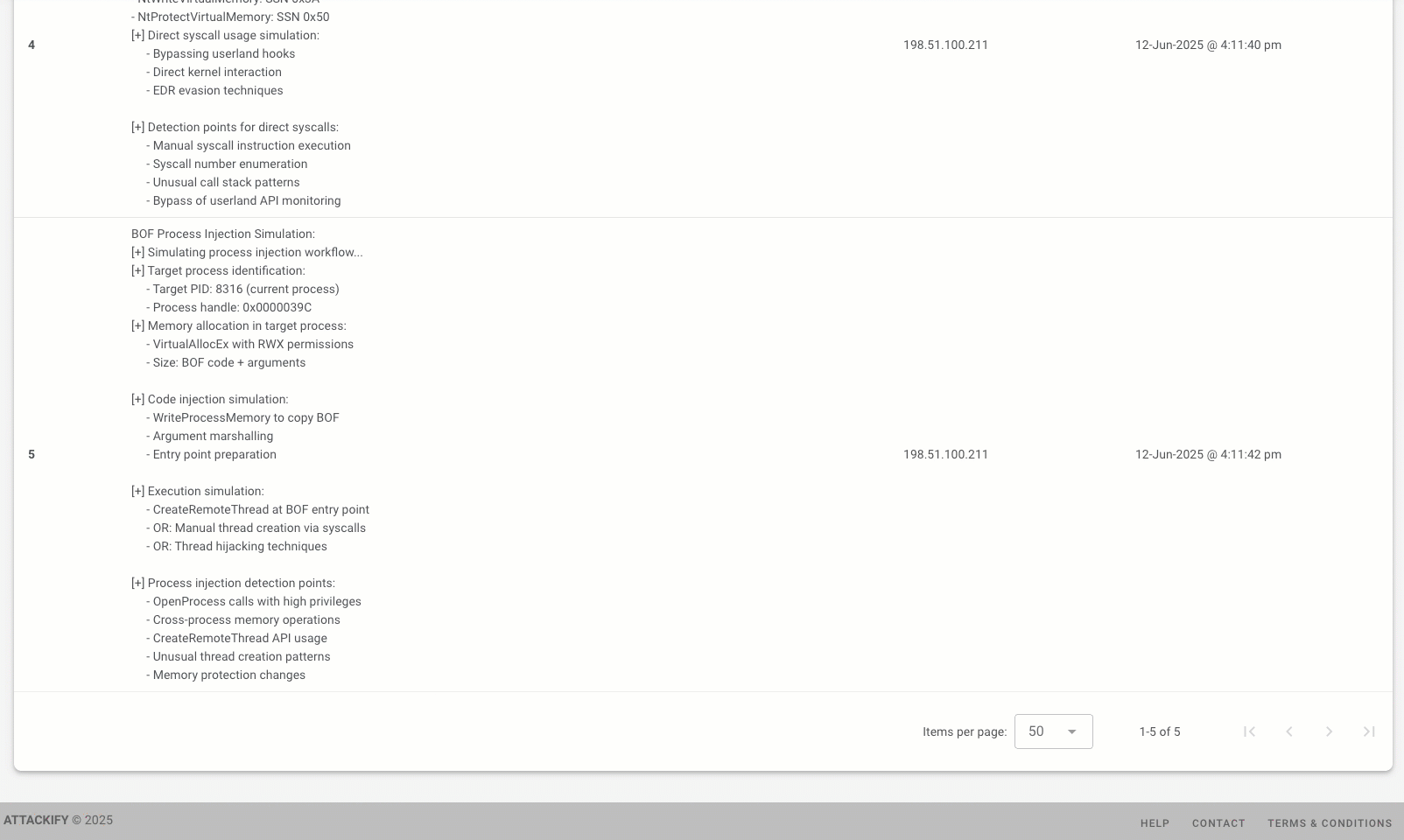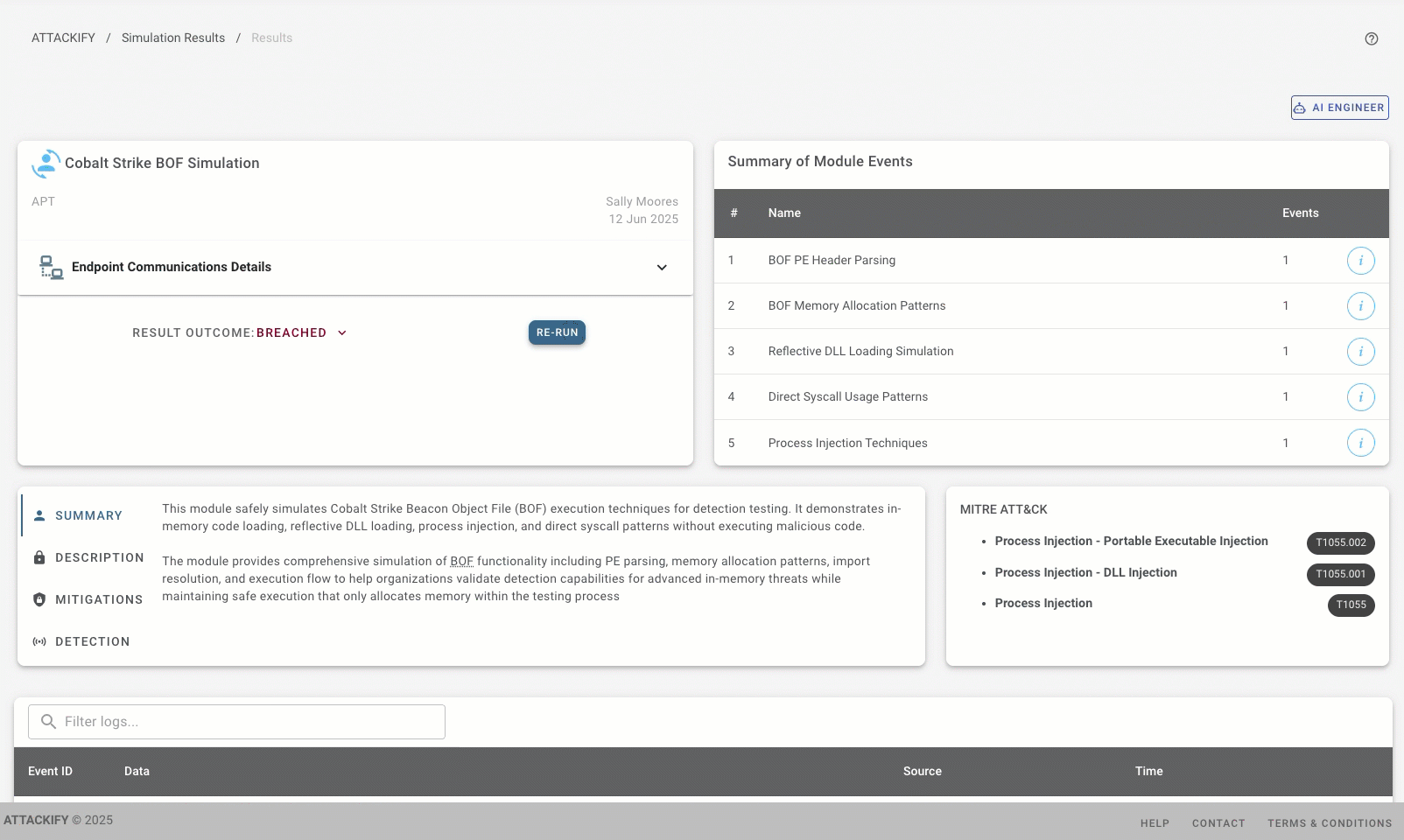
✅ PE Parsing Simulation
- - Mimics how BOFs analyze executable headers (like calc.exe)
- - Demonstrates IMAGE_DOS_SIGNATURE and IMAGE_NT_SIGNATURE parsing
- - Triggers EDR alerts for suspicious PE examination patterns
✅ Memory Management Patterns
- - Simulates VirtualAlloc/HeapAlloc calls characteristic of BOF loaders
- - emonstrates RWX memory allocation patterns that SOCs should monitor
- - Shows memory protection changes that indicate in-memory code execution
✅ Reflective Loading Techniques
- - Reproduces manual DLL loading without LoadLibrary APIs
- - Simulates GetProcAddress enumeration patterns
- - Demonstrates position-independent code execution
✅ Direct Syscall Simulation
- - Shows how advanced BOFs bypass userland API hooks
- - Demonstrates NTDLL direct call patterns
- - Highlights detection gaps in traditional API monitoring
✅ Process Injection Patterns
- - Simulates cross-process code injection techniques
- - Demonstrates thread hijacking and APC injection methods
- - Shows memory allocation in remote processes
Module 2: TrustedSec BOF Situational Awareness
Building on TrustedSec’s legendary CS-Situational-Awareness-BOF repository (1,400+ GitHub stars!), this module simulates their most popular reconnaissance BOFs:
✅ Advanced whoami BOF
- - Simulates
GetTokenInformationandLookupAccountSidAPI calls - - Demonstrates domain enumeration patterns
- - Shows privilege escalation reconnaissance techniques
✅ Enhanced netuser BOF
- - Reproduces
NetUserEnumandNetLocalGroupEnumpatterns - - Simulates advanced LDAP query sequences
- - Demonstrates user account enumeration techniques
✅ Comprehensive tasklist BOF
- - Uses
CreateToolhelp32Snapshotfor process analysis - - Shows WMI query patterns:
"SELECT * FROM Win32_Process" - - Demonstrates security process reconnaissance
✅ Advanced dir BOF
- - Simulates FindFirstFile/FindNextFile enumeration
- - Shows ACL enumeration and file attribute analysis
- - Demonstrates advanced file system reconnaissance
✅ System Information Gathering
- - Reproduces comprehensive system API calls
- - Shows registry and environment enumeration
- - Demonstrates hardware fingerprinting activities
What Makes Our Simulations Special?
Authentic Detection Triggers
Unlike basic simulation tools, our modules trigger real detection events (safely) that your EDR should catch:
- - Unbacked RWX memory allocations
- - Systematic API enumeration patterns
- - Cross-process memory operations
- - Suspicious registry access patterns
Safe Learning Environment
- - No actual malware deployment
- - Controlled execution with detailed logging
- - Perfect for purple team exercises
- - Comprehensive MITRE ATT&CK mapping
Real-World Accuracy
Based on extensive research from Elastic Security Labs, IBM X-Force, and the security community, our simulations reflect actual BOF behavior patterns observed in the wild.
Perfect for Purple Team Excellence
For Red Teams:
- - Test realistic BOF techniques safely
- - Validate evasion capabilities
- - Practice advanced post-exploitation scenarios
For Blue Teams:
- - Train SOC analysts on BOF detection
- - Test EDR configuration effectiveness
- - Develop custom detection rules
For Purple Teams:
- - Collaborative improvement exercises
- - Gap analysis of detection capabilities
- - Incident response procedure validation
The Detection Game Plan
Our simulations help you build detection capabilities across multiple layers:
Memory-Based Detection
Test your tools’ ability to spot:
- - Unbacked executable memory regions (primary BOF indicator)
- - Memory allocation pattern analysis
- - Cross-process memory operations
API Monitoring Enhancement
Validate detection of:
- - Systematic
GetProcAddressenumeration - - Direct syscall patterns (advanced evasion)
- - Memory protection change sequences
Behavioral Analytics
Improve detection of:
- - Rapid symbol resolution activities
- - In-memory code loading patterns
- - Anomalous process behavior chains
The Bottom Line
BOF techniques represent a significant shift in post-exploitation methods. While threat actors have embraced these advanced capabilities, many internal security teams lack effective ways to test their defenses. ATTACKIFY’s simulation modules bridge this gap, providing realistic, continuous and safe training environments that prepare your team for real-world attack encounters.
Ready to level up your defenses? Our simulation modules are available now, FREE to all ATTACKIFY customers. Don’t wait for a real attack to discover your detection gaps, start testing today!
Because in cybersecurity, practice doesn’t make perfect, but it sure beats learning during an actual breach!