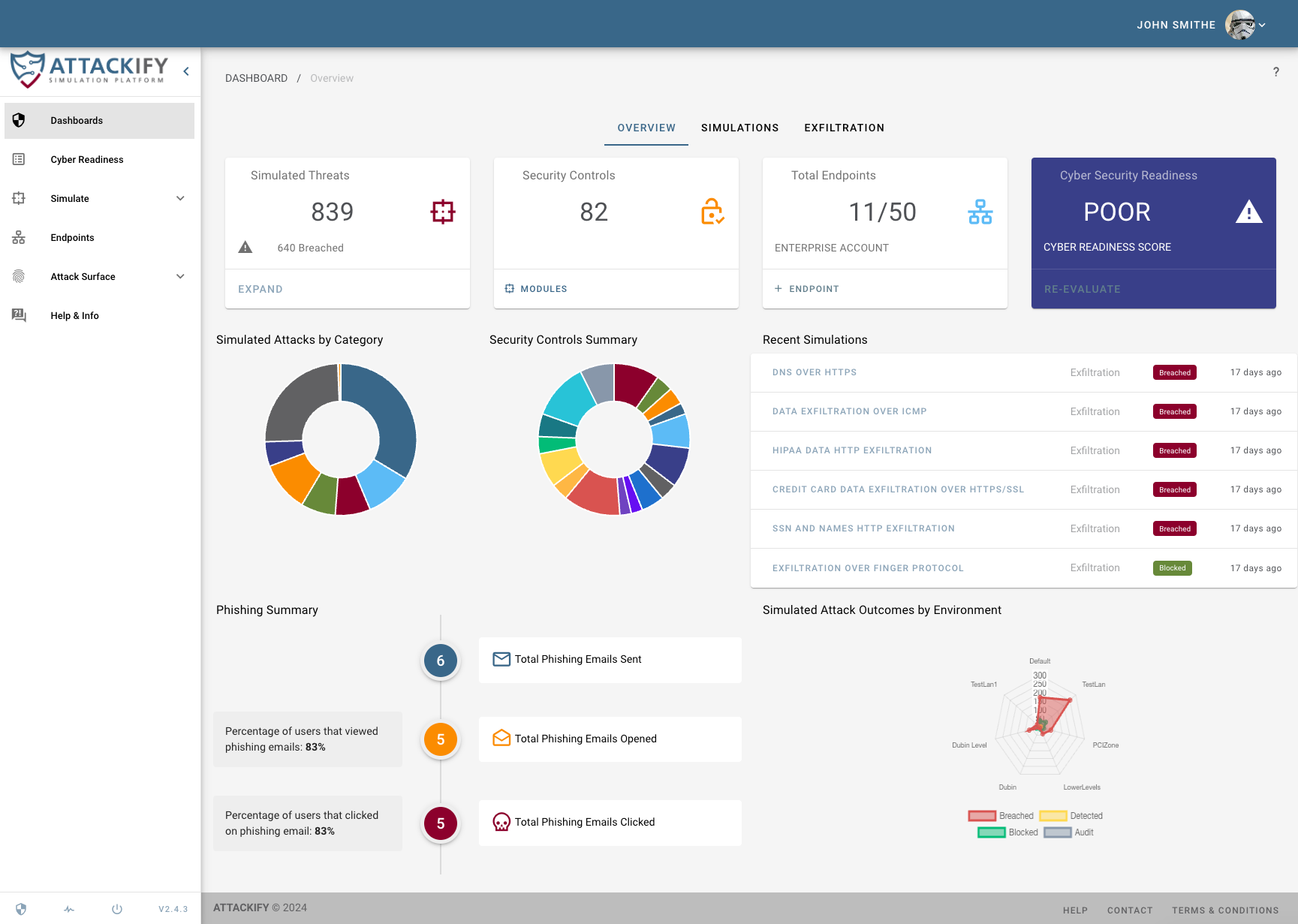
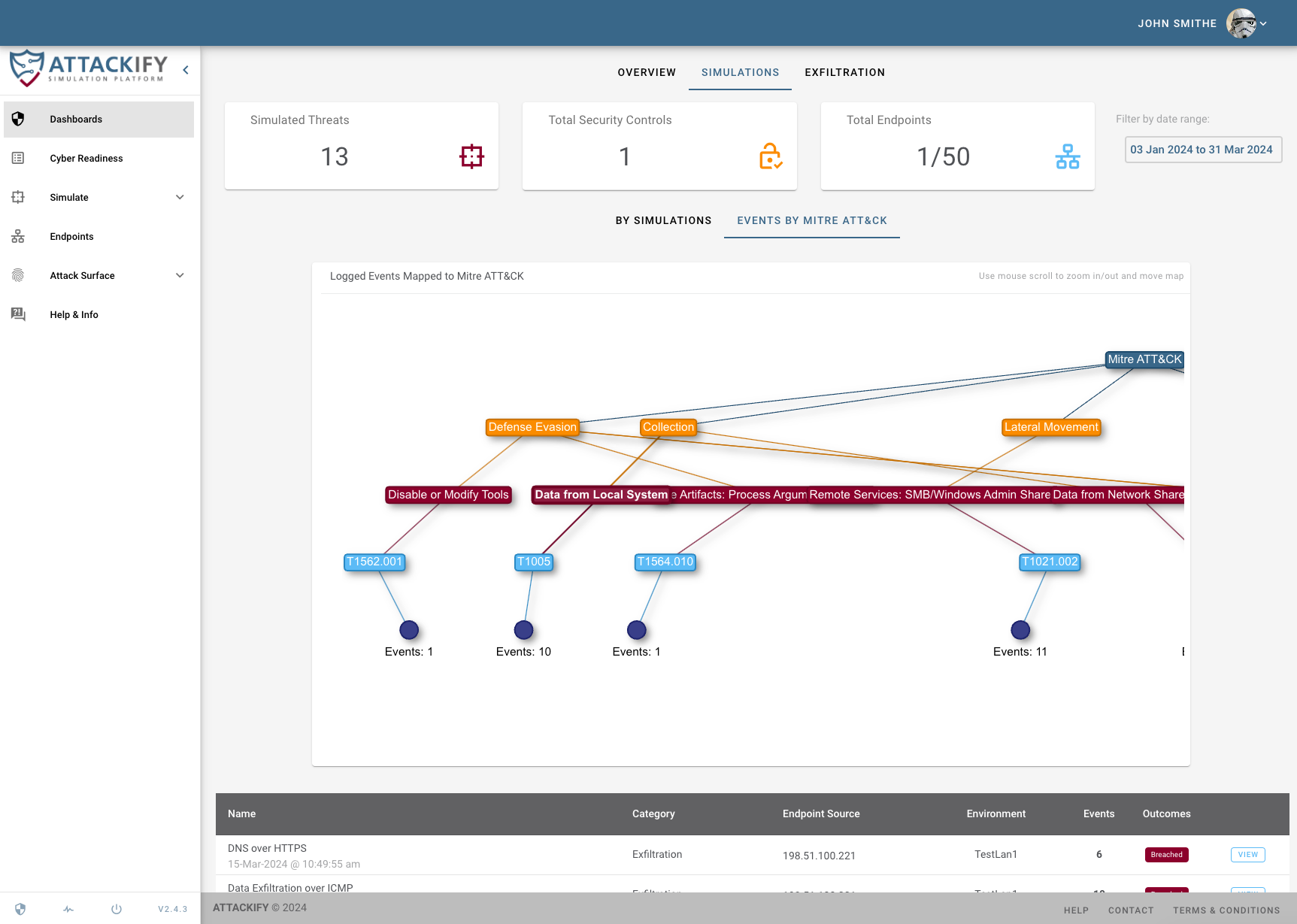
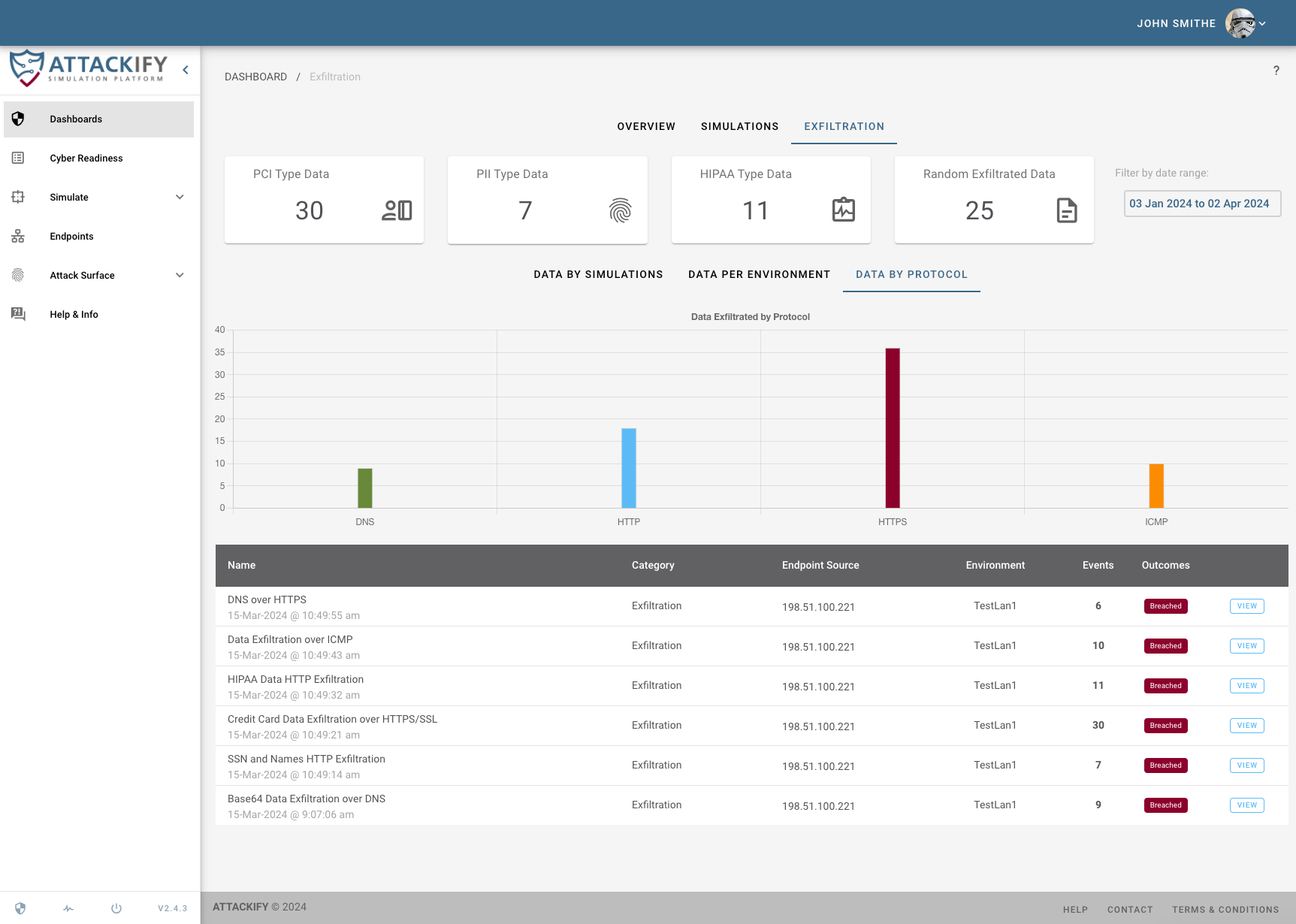
For many organizations, the first time they truly understand their cyber security posture is when they experience an actual cyber attack. In reality many DEFENDERS may not be exposed to the various TACTICS, TECHNIQUES, or PROCEDURES that attackers use unless its during an actual ATTACK.
That’s where ATTACKIFY comes in!
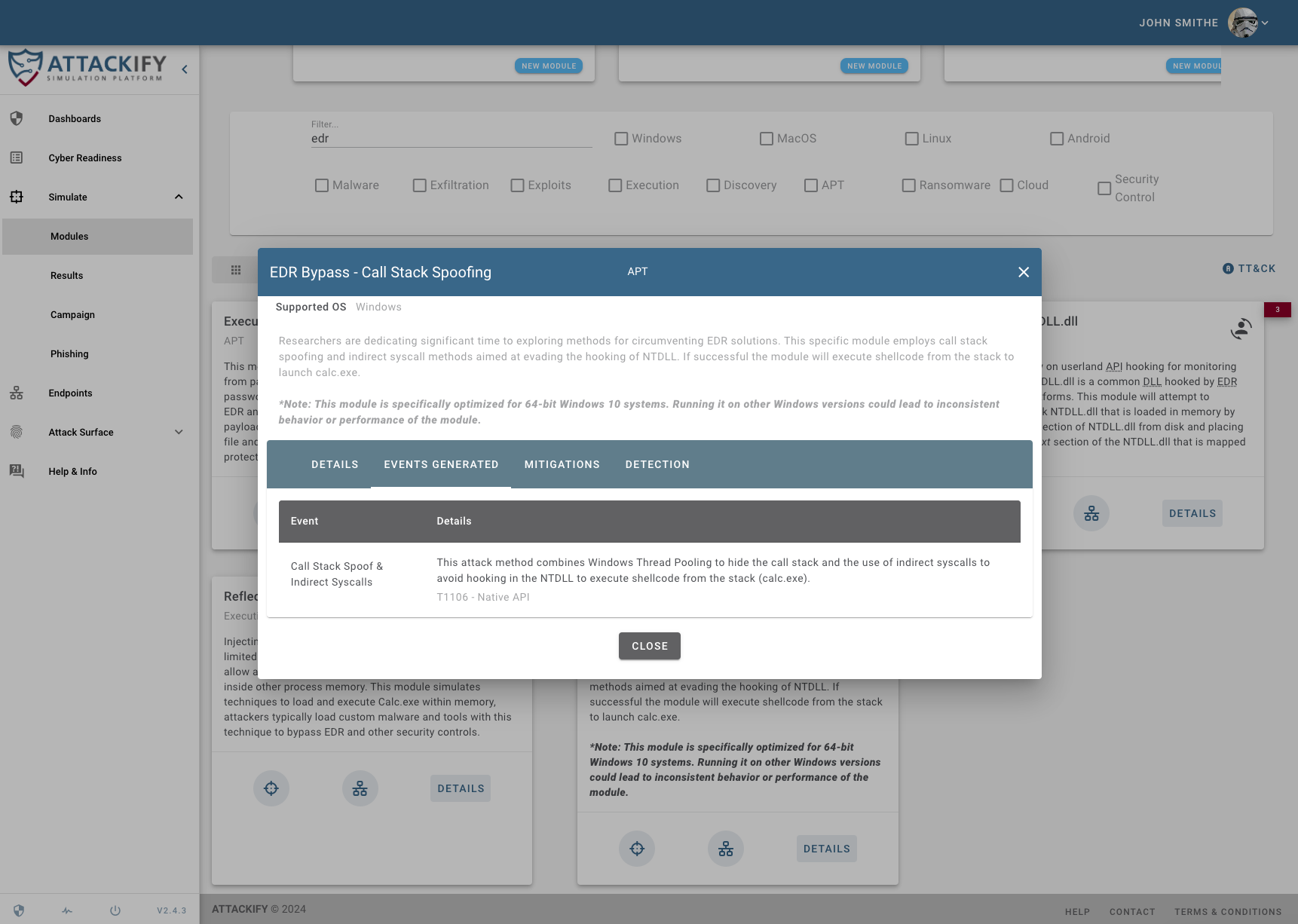
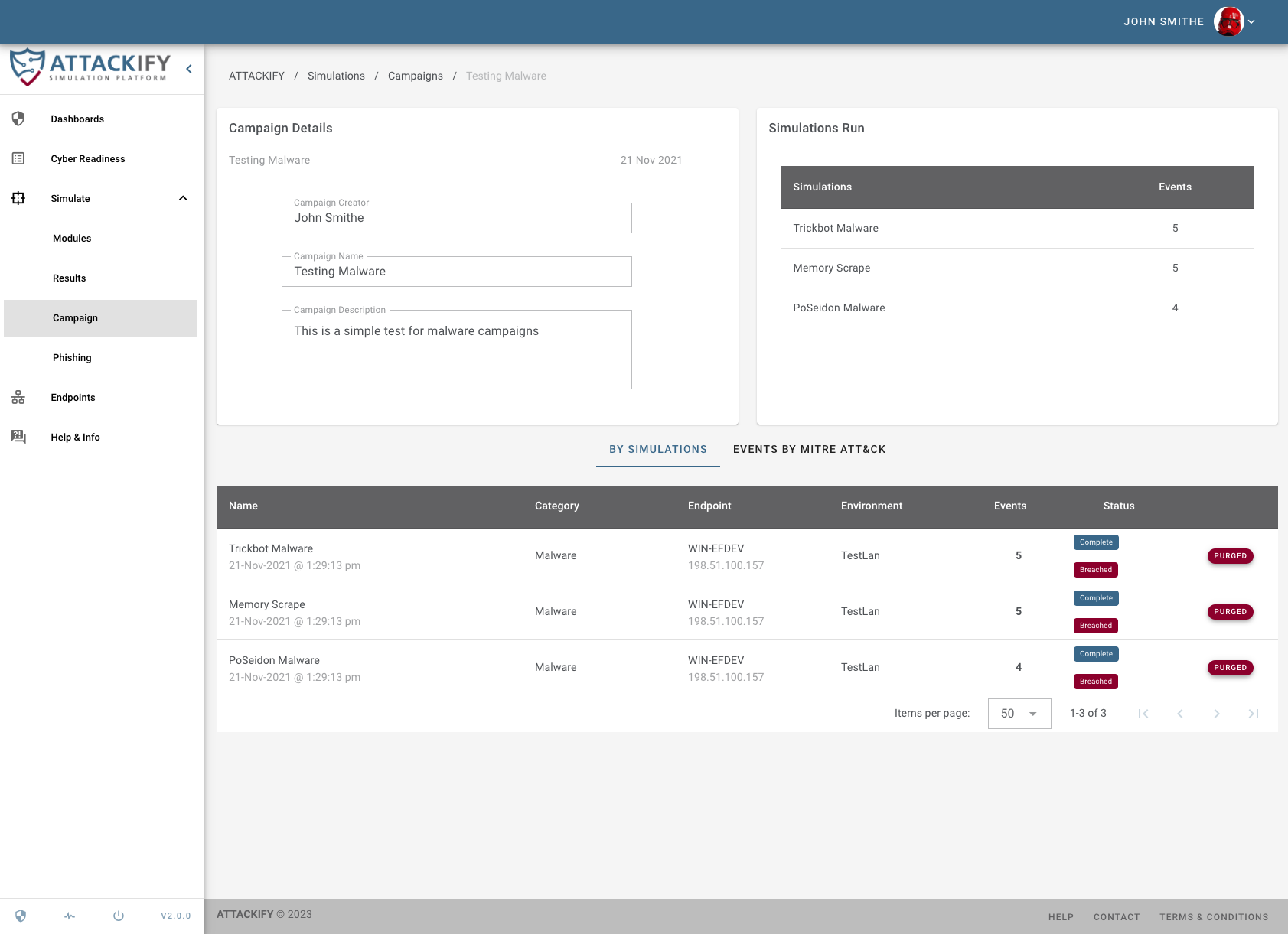
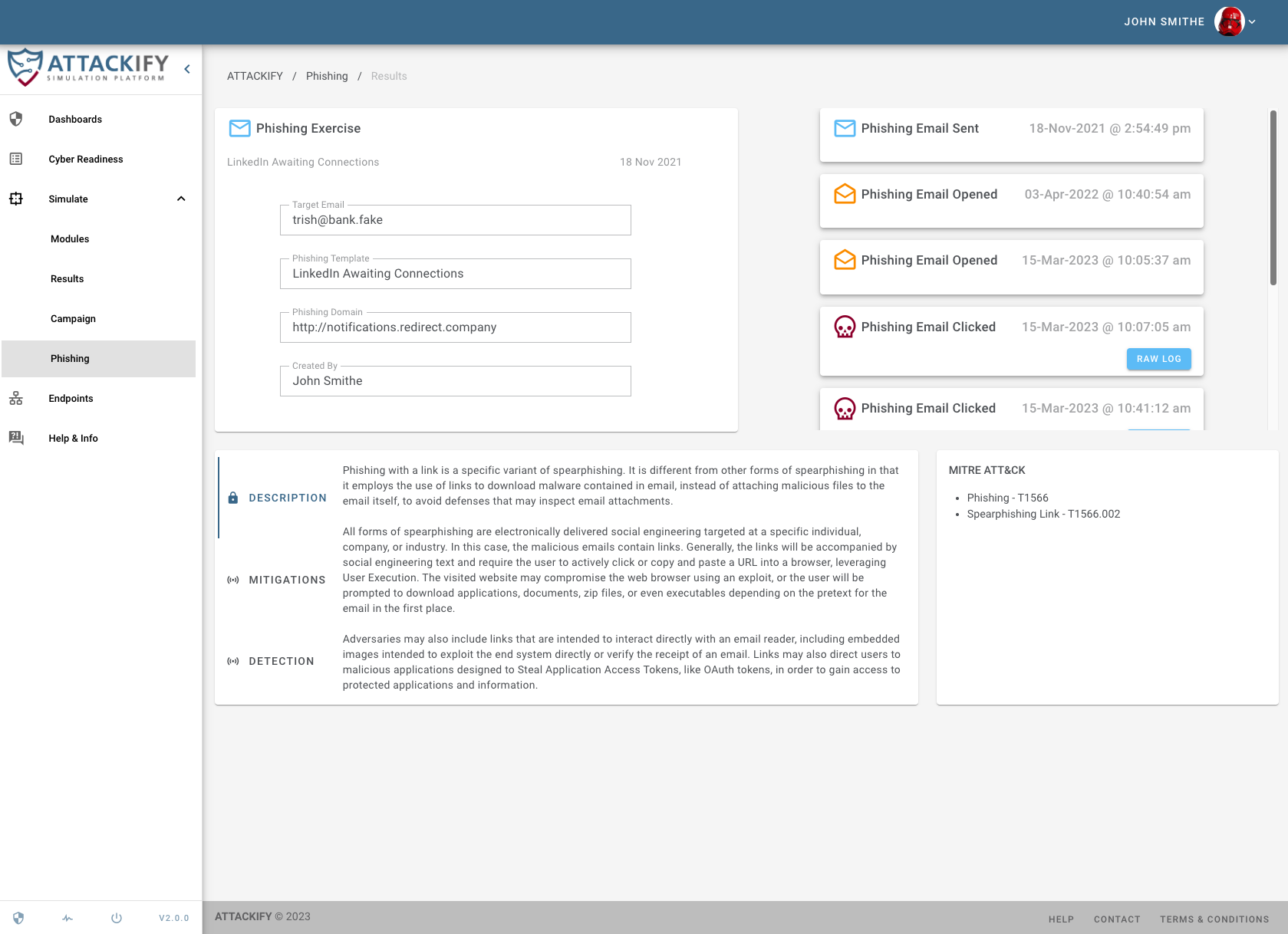
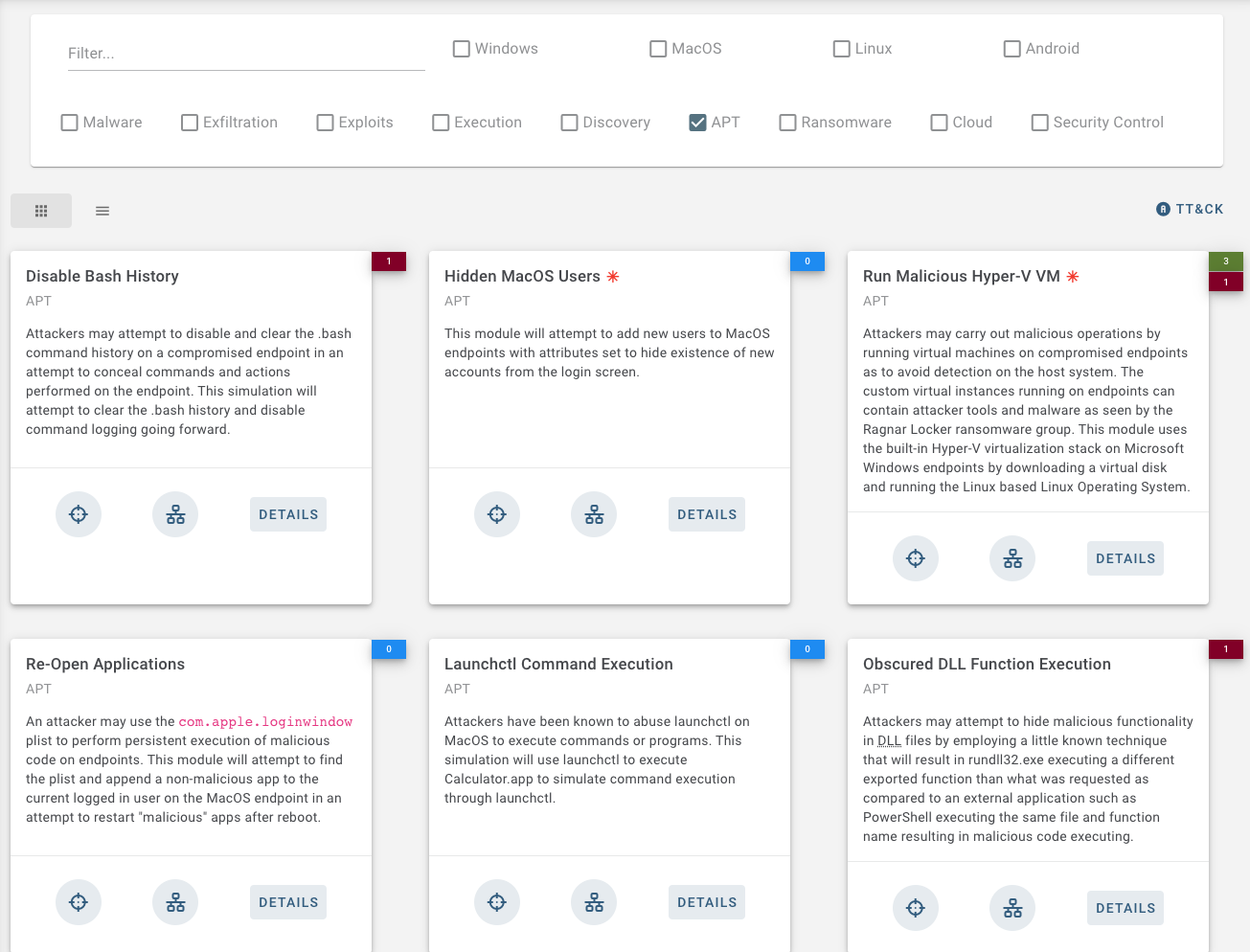
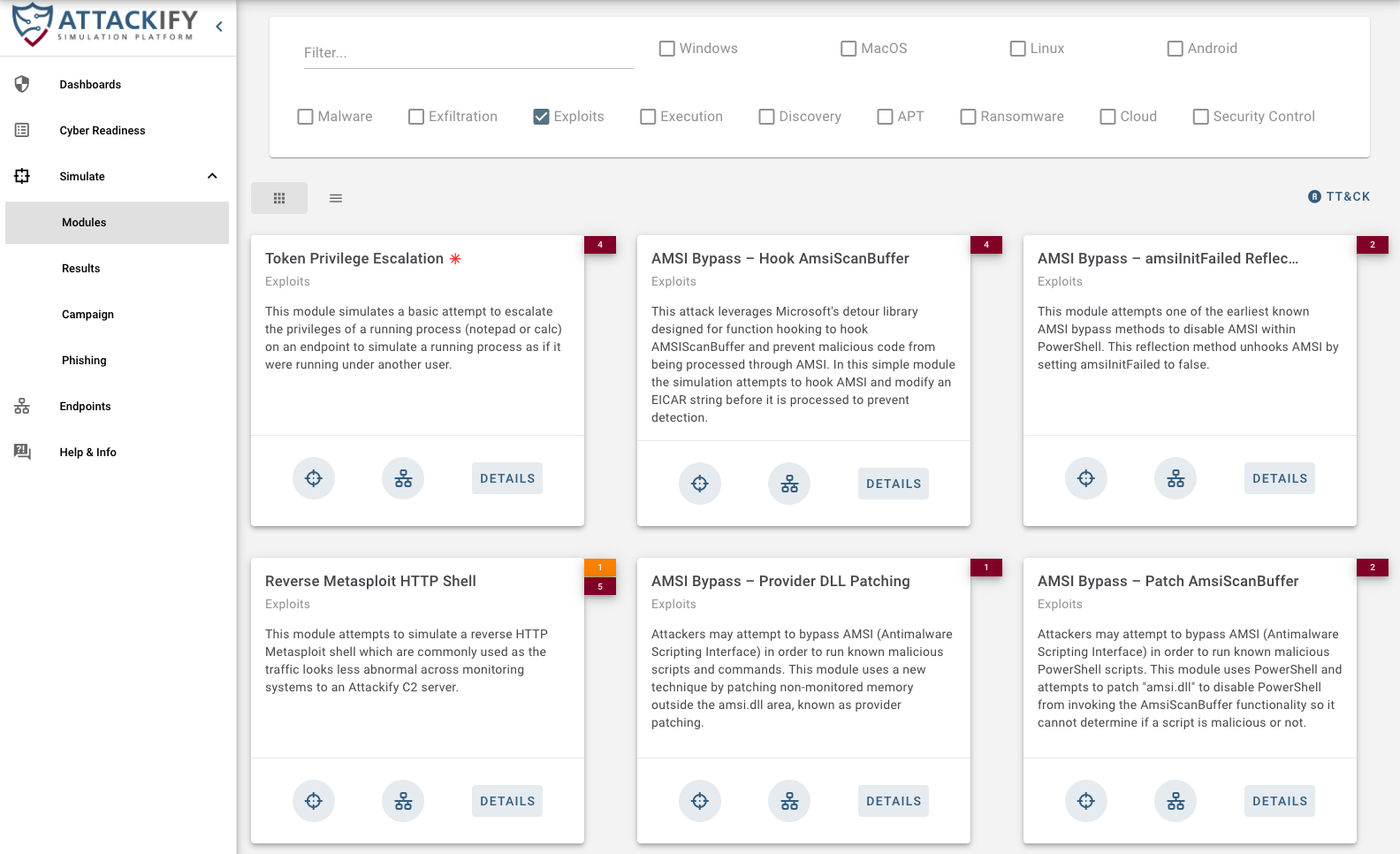
Our platform is initially designed to help organizations understand what Advanced Persistent Threats (APTs) look like by simulating REAL THREATS on your endpoints.
This enables security teams to see through the eyes of an ATTACKER but with the lens of a DEFENDER.This will enable you to identify security BLINDSPOTS, strengthen SECURITY CONTROLS and keep the Security Operations team CYBER FIT.
ATTACKIFY is an easy to use and affordable online BREACH & ATTACK simulation platform, primarily a cloud-based solution to run and manage attack simulation modules, security audits and phishing simulations with remote endpoint agents safely inside your environments.
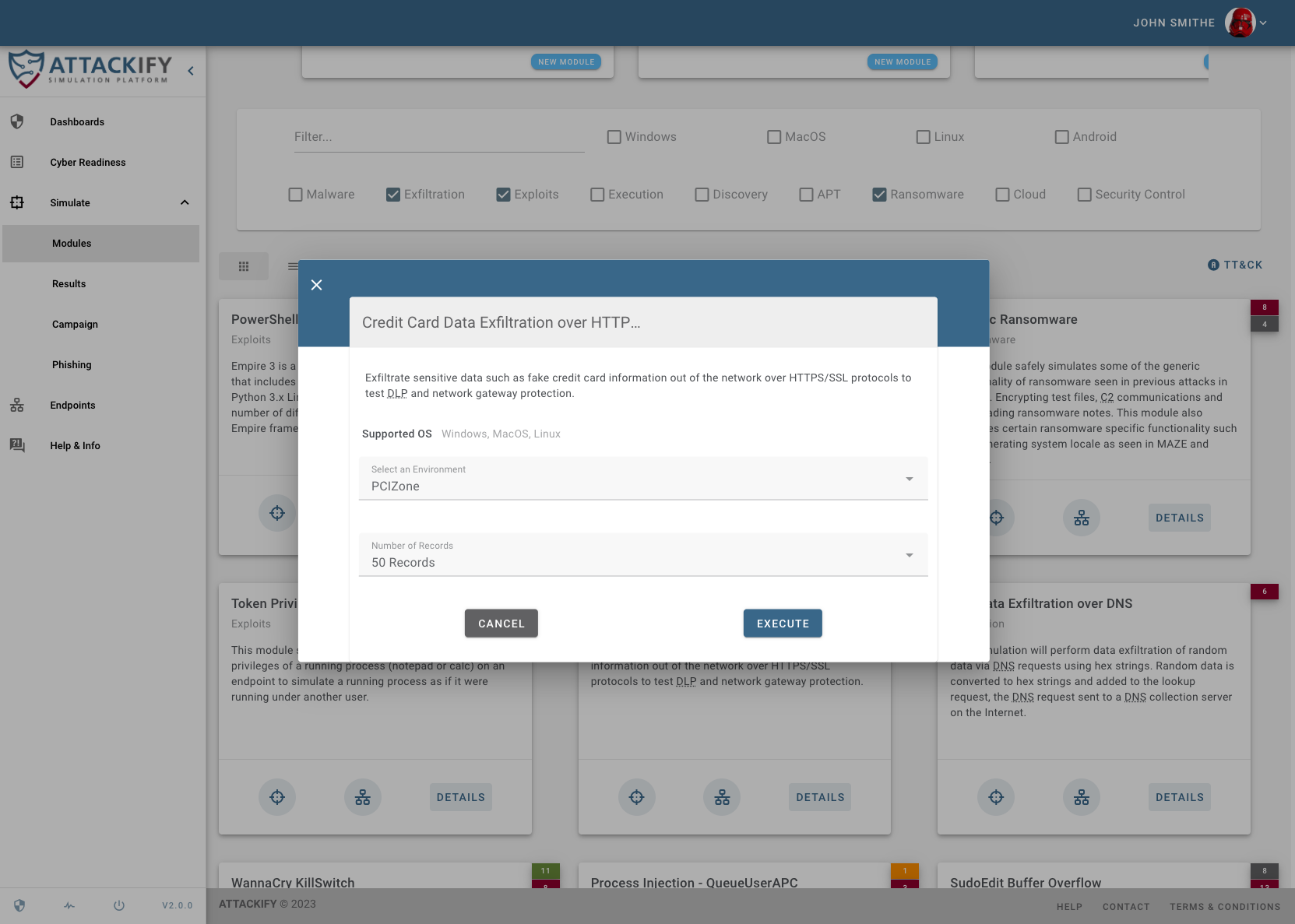
ATTACKIFY is a powerful online platform designed to streamline the process of conducting BREACH & ATTACK simulations. With just a few clicks, users can log in, run an endpoint agent, select a module, and execute their first attack.
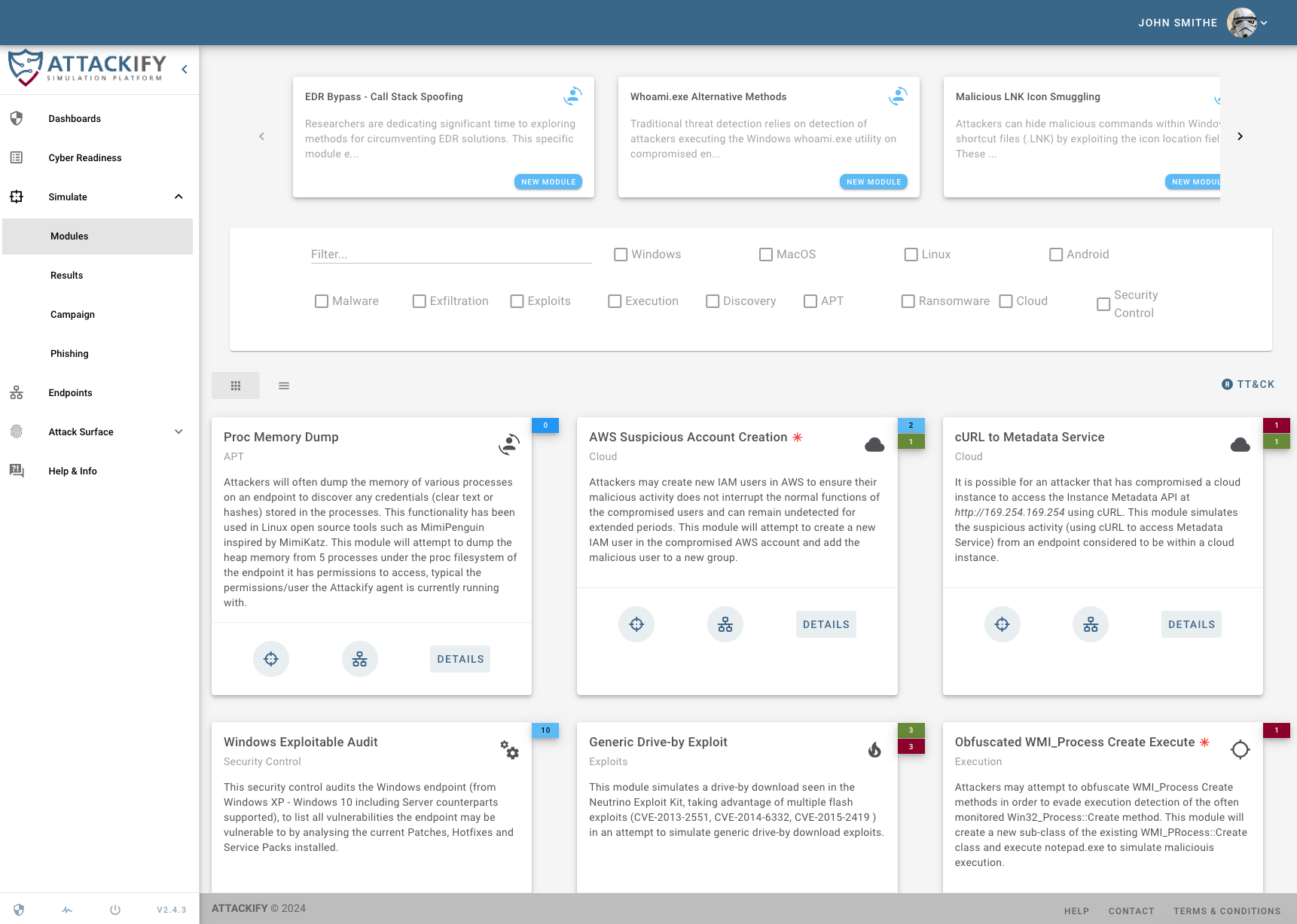
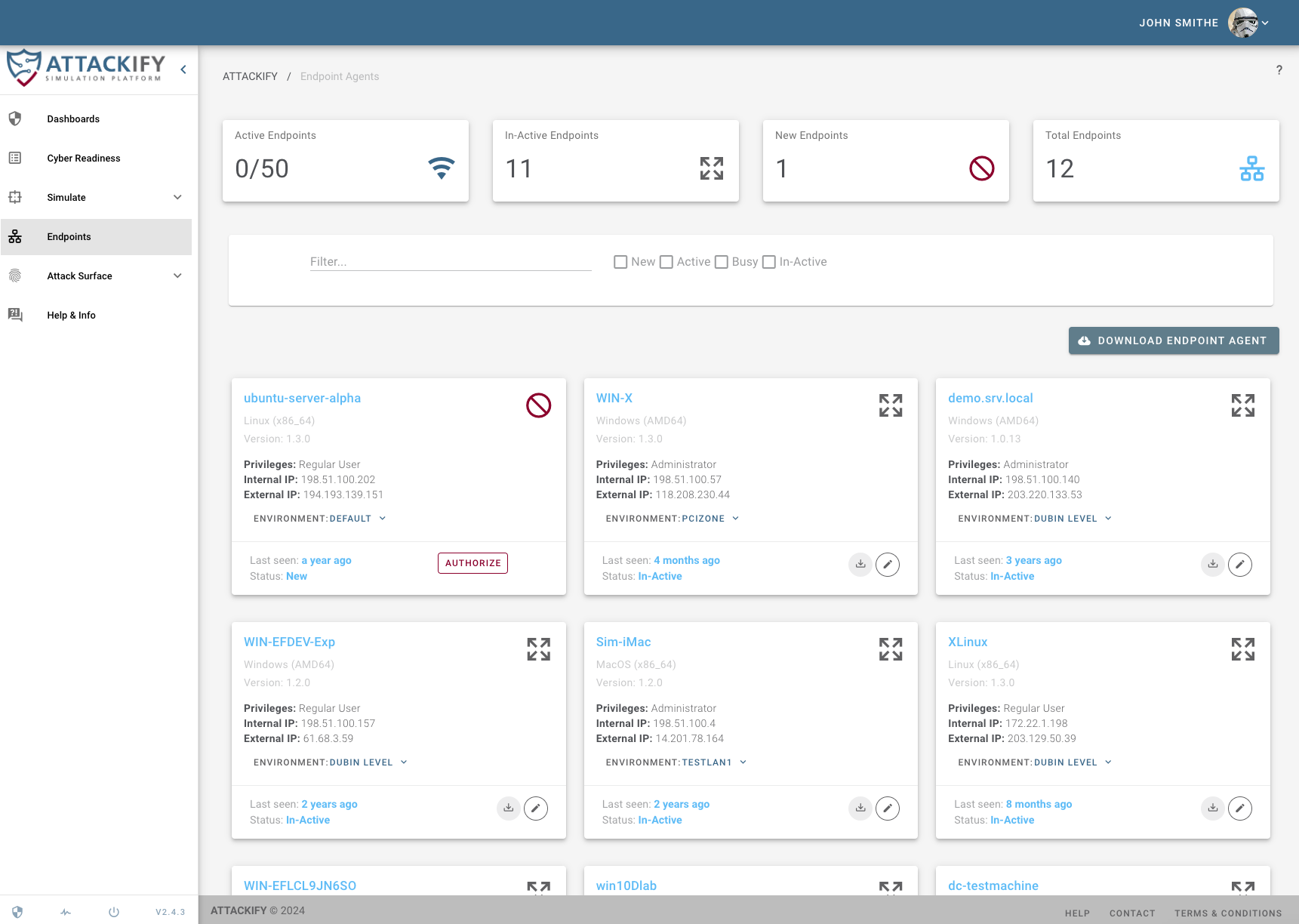
Endpoint Agents run from systems you choose to test security controls from. Running an endpoint agent allows you to run any available attack/security control modules within ATTACKIFY. We currently support Windows, Linux, MacOS & Android (closed beta).
We believe that simplicity is the key to effective value adding solutions. ATTACKIFY is purpose-built to be intuitive, streamlined, and free of unnecessary complexity & features. ATTACKIFY gives you exactly what you need to get the job done quickly and easily.
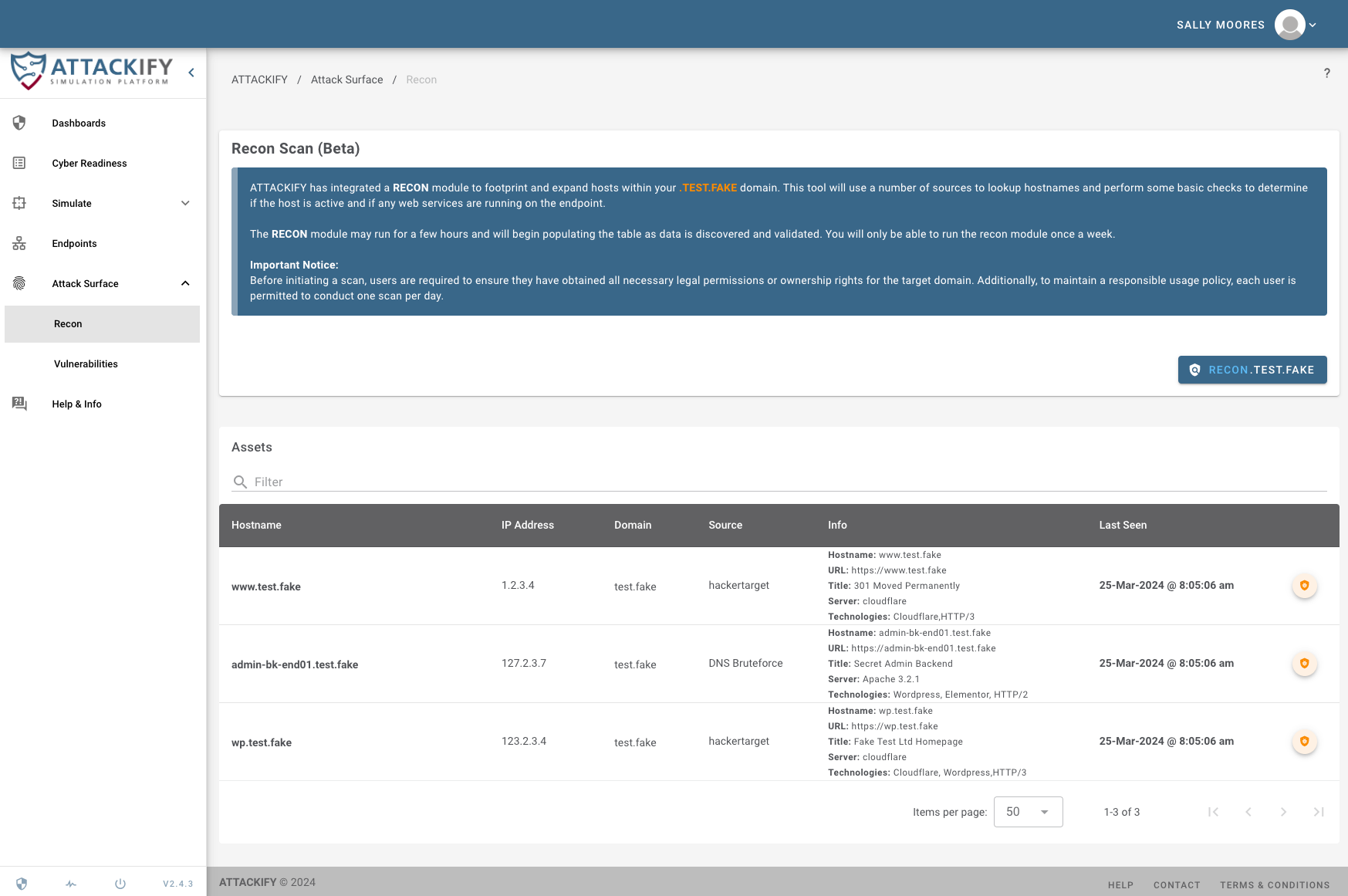
ATTACKIFY is not just about running cyber attack modules. Additional features include:
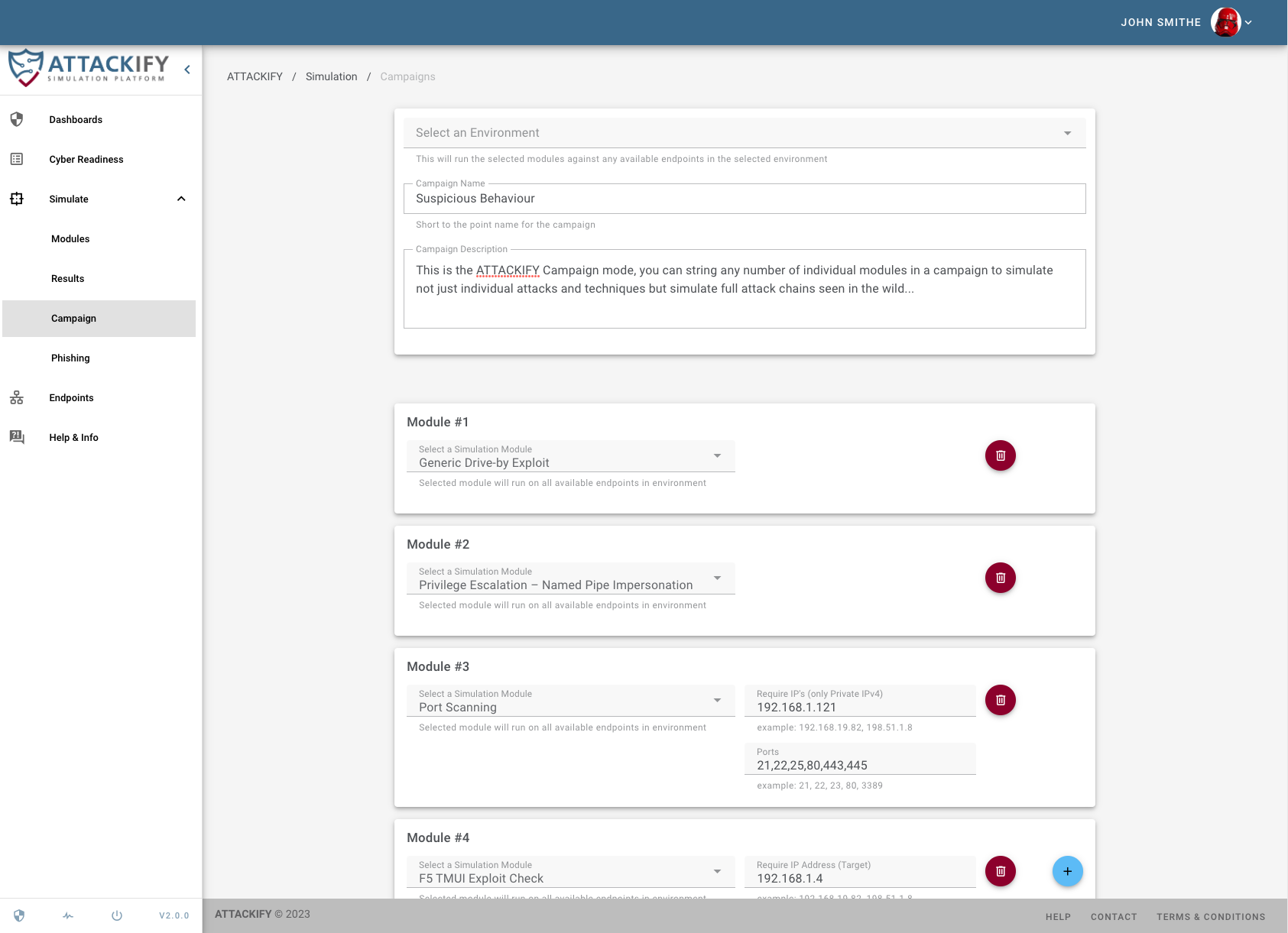
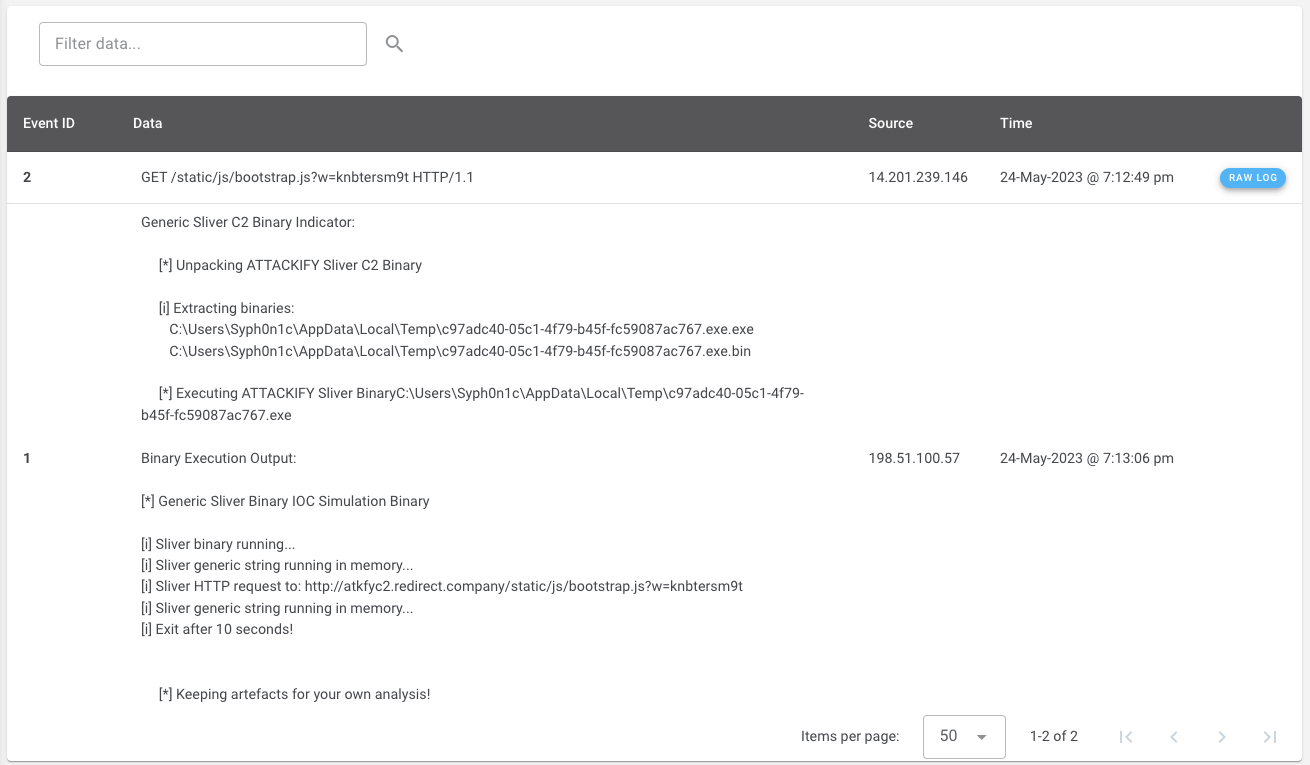
Use ATTACKIFY to execute cyber threats safely'ish within your environment:
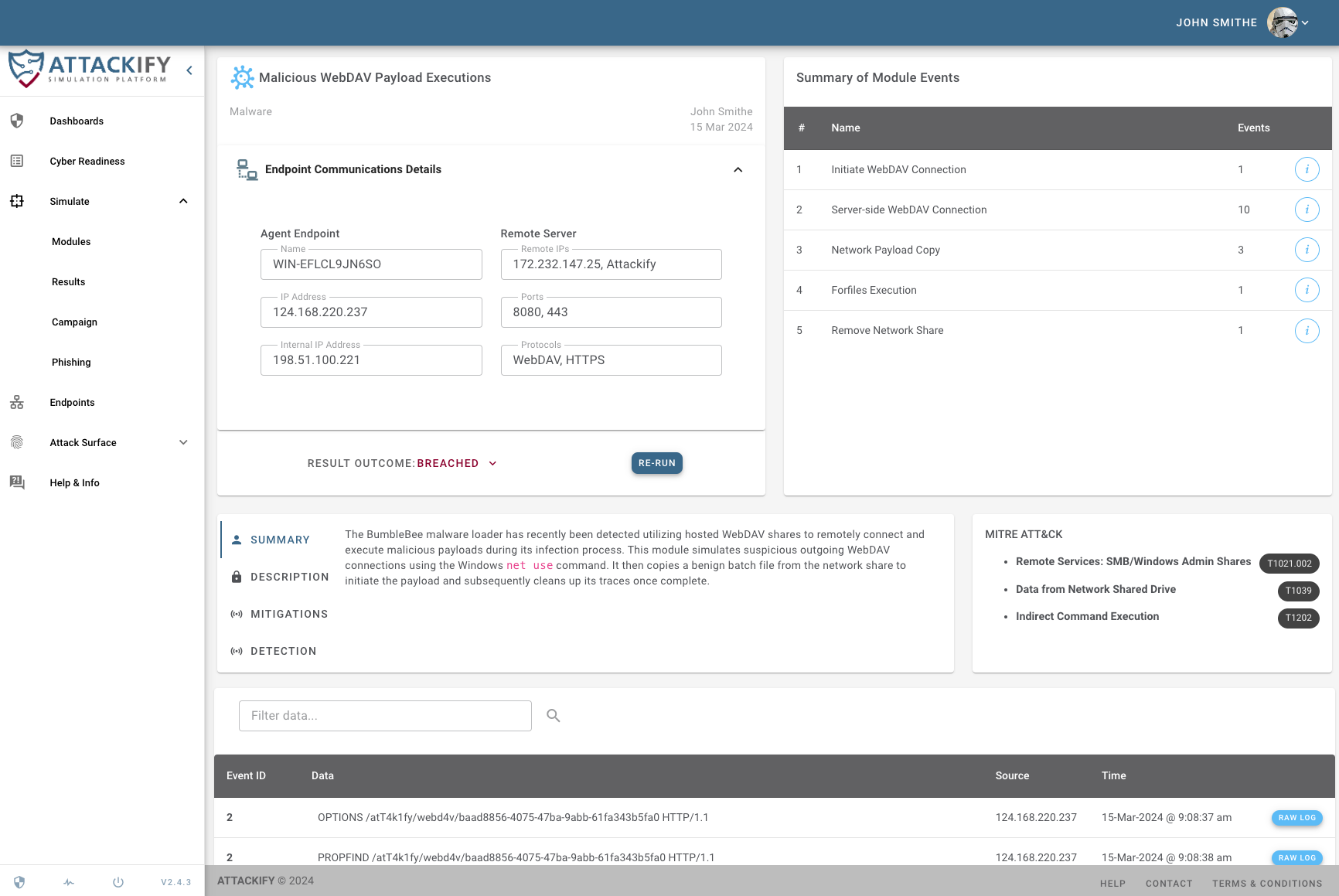
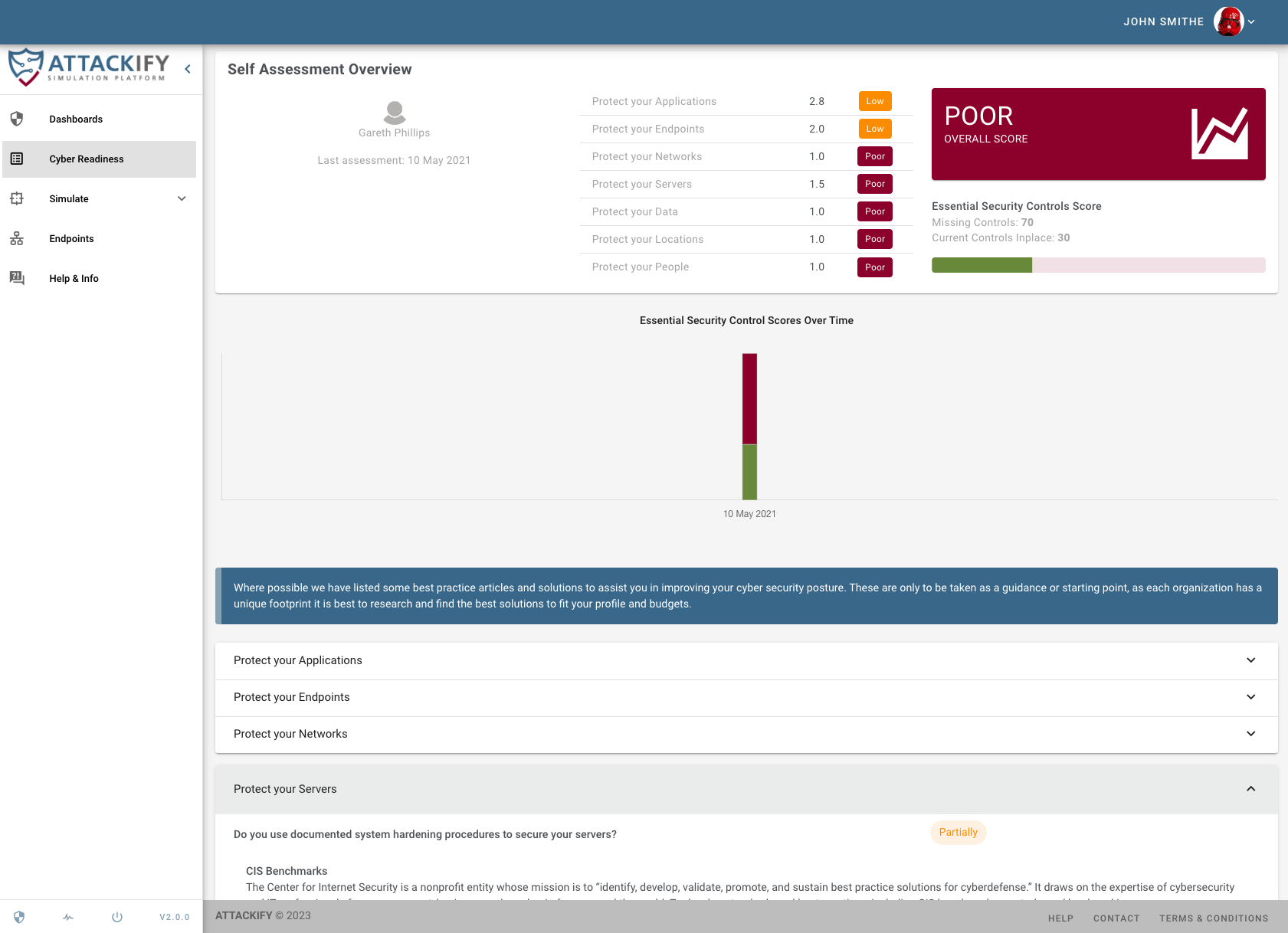
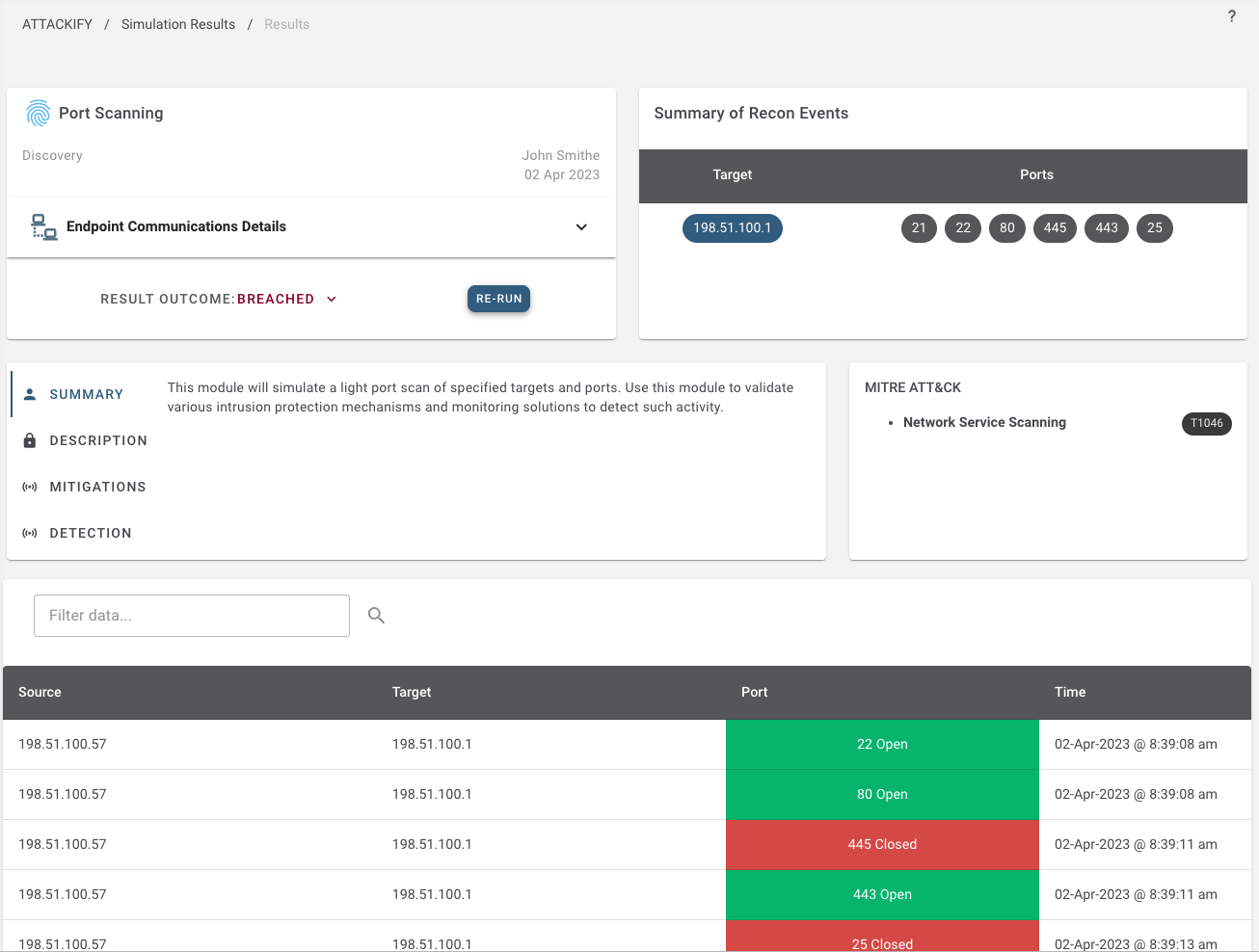
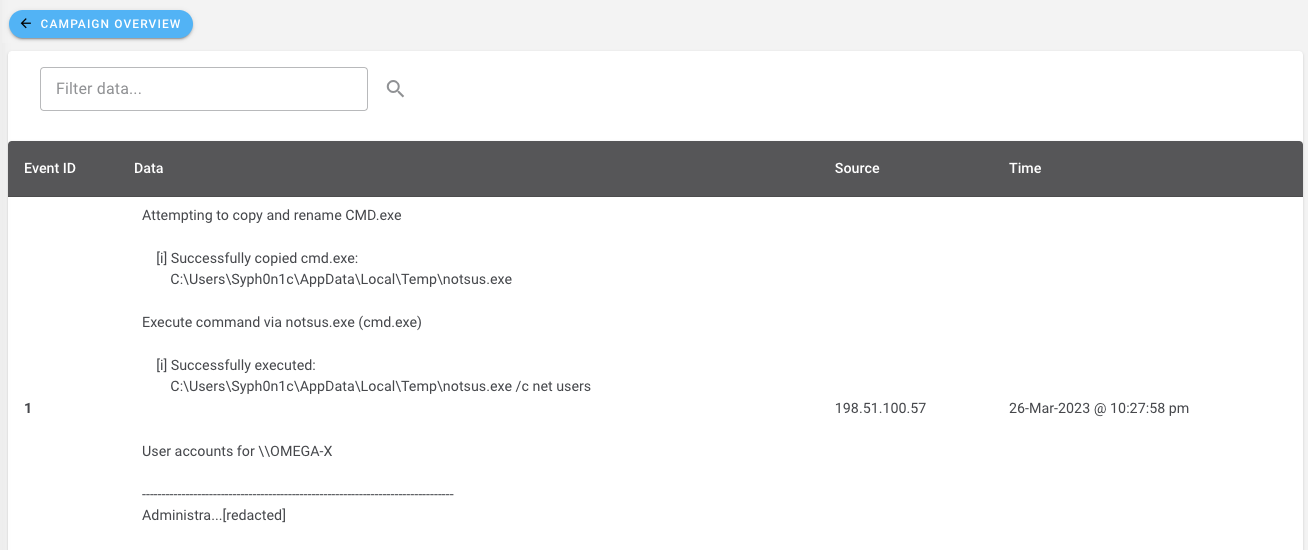
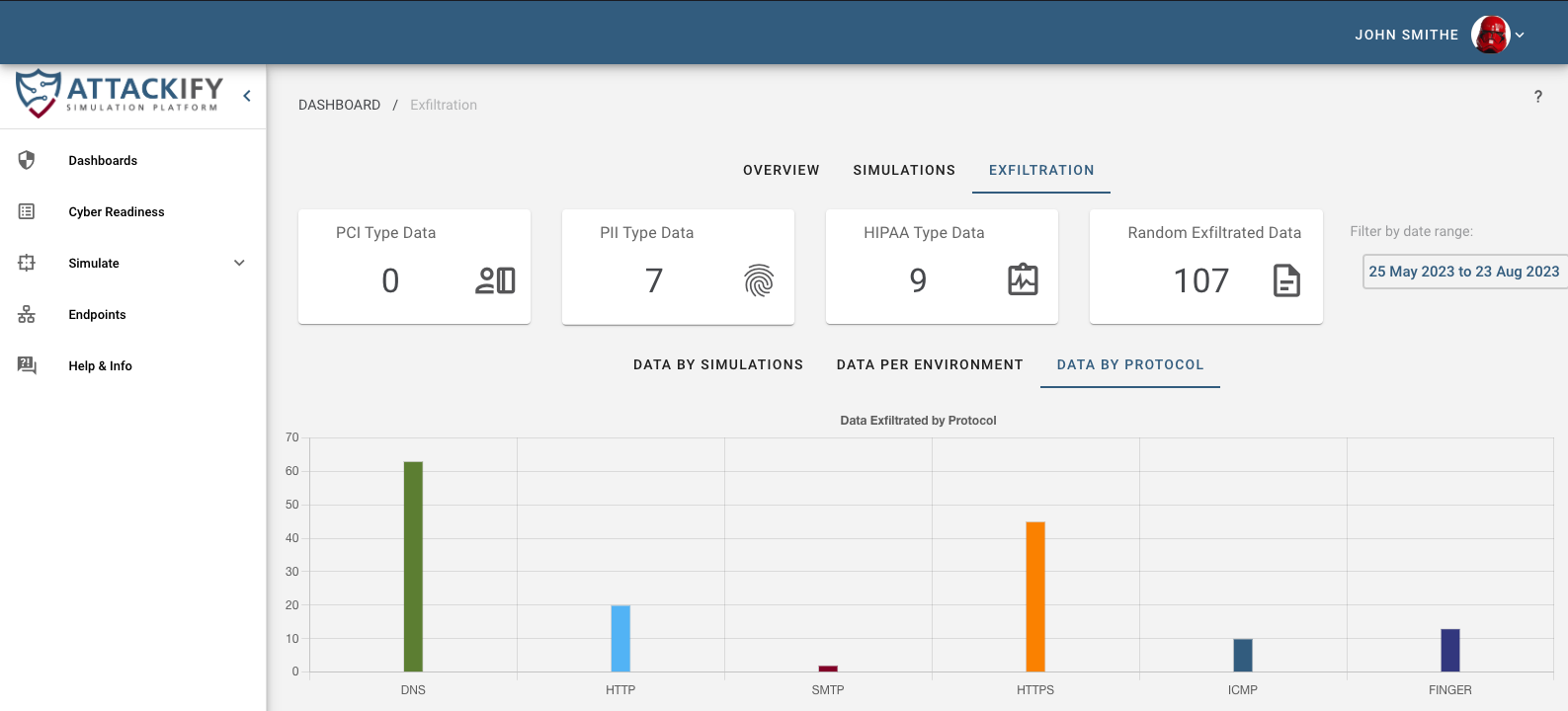
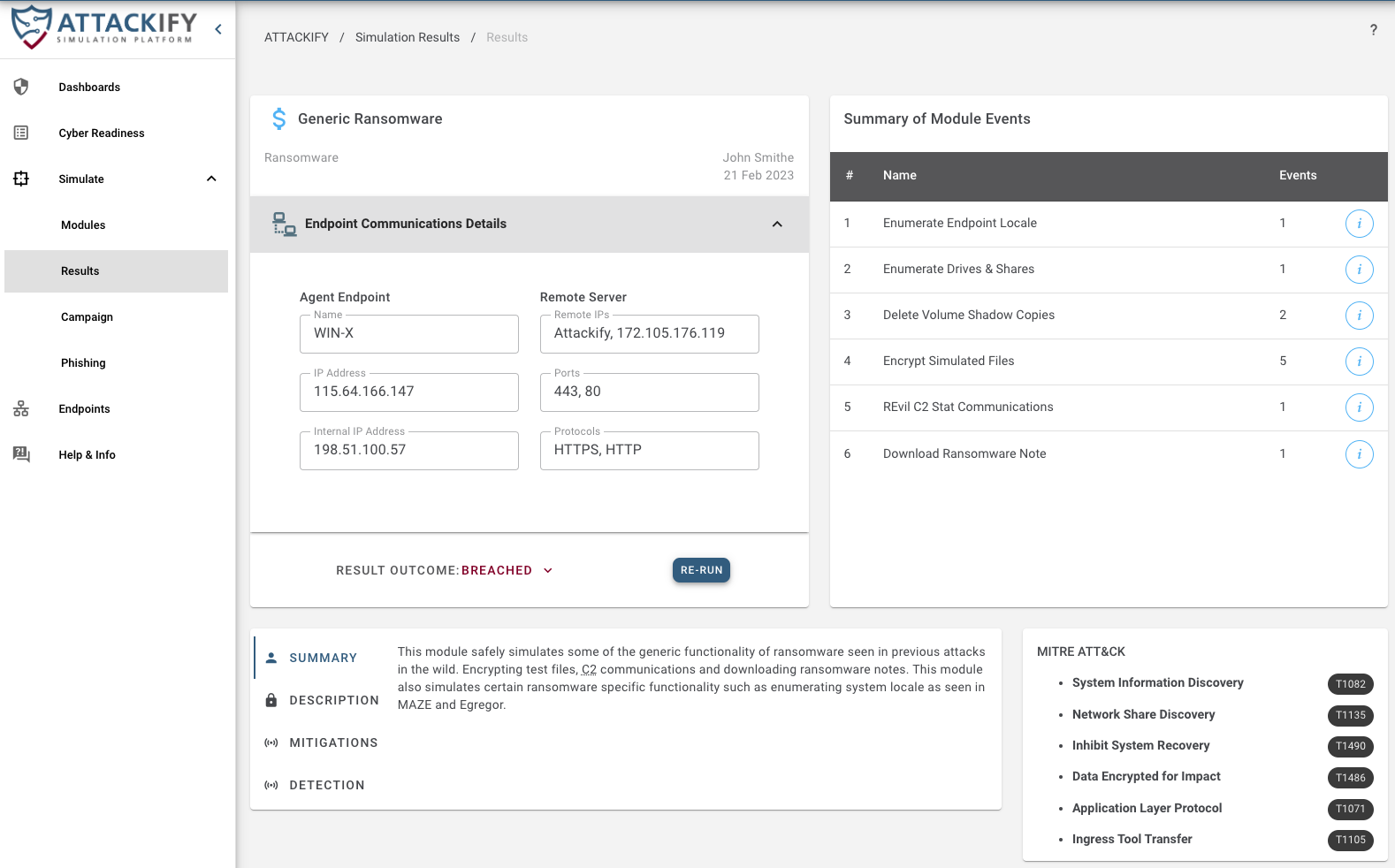
Included in all attack and security control modules, ATTACKIFY provides:
Breach & Attack Simulation doesn’t get any easier than ATTACKIFY . If you have ever tried to setup and use Atomic Red (which is great by the way) or try find your way through a really expensive and complex BAS solution and just want to get to the good stuff, then ATTACKIFY is for you.
ATTACKIFY is designed to be easy to use and easy to understand. We have taken the complexity out of the platform so you can focus on running ATTACK simulations. Login, download and run an endpoint agent, select a module and run it. It’s that simple.
ATTACKIFY is designed to be used by anyone, from the most junior analyst to the most senior security professional, even your CISO could run ATTACKIFY.